Rocheston Cybersecurity Framework (RCF) is a future-first cyber-resilience architecture designed to move organizations beyond checkbox compliance into continuous, provable security.
RCF is built as a superset of global cybersecurity and assurance standards. Organizations that meet RCF requirements inherently satisfy the intent and technical safeguards of leading frameworks such as NIST SP 800-53, ISO/IEC 27001, SOC 2, HIPAA, and PCI DSS—while also gaining protection for modern and emerging risk domains those standards do not fully address.
Unlike legacy frameworks that were designed for static infrastructure and periodic audits, RCF is engineered for environments that change constantly. It integrates post-quantum security planning, autonomous AI governance, continuous verification, and proof-grade evidence into a single, cohesive operating model.
RCF does not ask you to prove compliance once a year. It enables you to prove resilience every day.
Implement Once. Comply Everywhere.
One unified security framework aligned with global standards and regional regulations—so a single implementation supports compliance across borders.
🔁 What “Implement Once. Comply Everywhere.” Means
Organizations today face a growing maze of compliance obligations. Beyond global frameworks like NIST, ISO, SOC 2, HIPAA, and PCI DSS, they must also meet government and regional regulations across multiple jurisdictions—such as Japan’s APPI, Singapore’s PDPA, Australia’s Essential Eight and Privacy Act, the UK’s NCSC and Cyber Essentials requirements, and the EU’s GDPR and NIS directives. While the names differ, the underlying expectations are often the same: strong governance, access control, monitoring, resilience, and provable security.
RCF is designed to unify these overlapping requirements into a single, modern control architecture. When an organization implements RCF, it establishes one set of enforced, measurable controls that align with the intent and technical safeguards demanded by multiple standards and government regulations simultaneously. Evidence is collected once, validated continuously, and reused across audits and regulatory assessments—rather than rebuilt for each country or framework.
This approach reduces duplication, minimizes audit fatigue, and simplifies cross-border compliance. Security teams focus on operating and improving real security, while regulatory adherence across regions becomes a natural byproduct of how the organization runs every day.
Implement once. Maintain continuously. Comply everywhere.
Proof, Not Promises
Auditors do not certify intentions. They certify evidence.
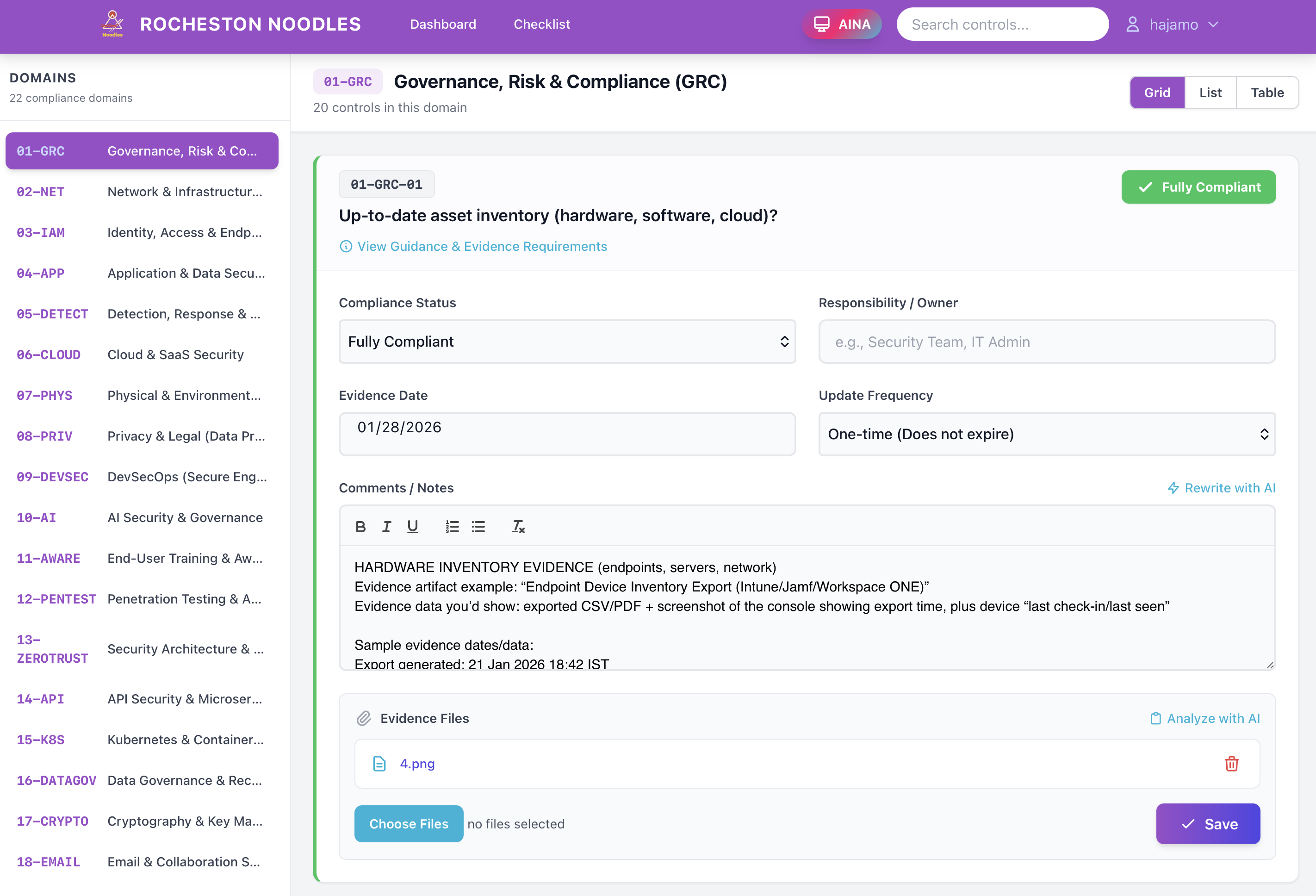
RCF is built around measurable control states and proof-grade artifacts. Instead of “we believe we are compliant,” RCF enables “we can prove we are compliant,” with traceable evidence that can be packaged and presented quickly.
Typical evidence outputs include:
- Access enforcement reports and periodic access reviews
- Change management approvals and traceable records
- Monitoring coverage metrics and alert quality
- Incident response timelines and lessons learned
- Vulnerability remediation tracking and closure
- Data protection proof (retention, encryption, key management)
Built for Global Regulation.
RCF aligns core security controls with government and regulatory expectations across the EU, UK, Japan, Singapore, Australia, and other regulated markets.
🤖 Operationalized by AINA and Rocheston Noodles
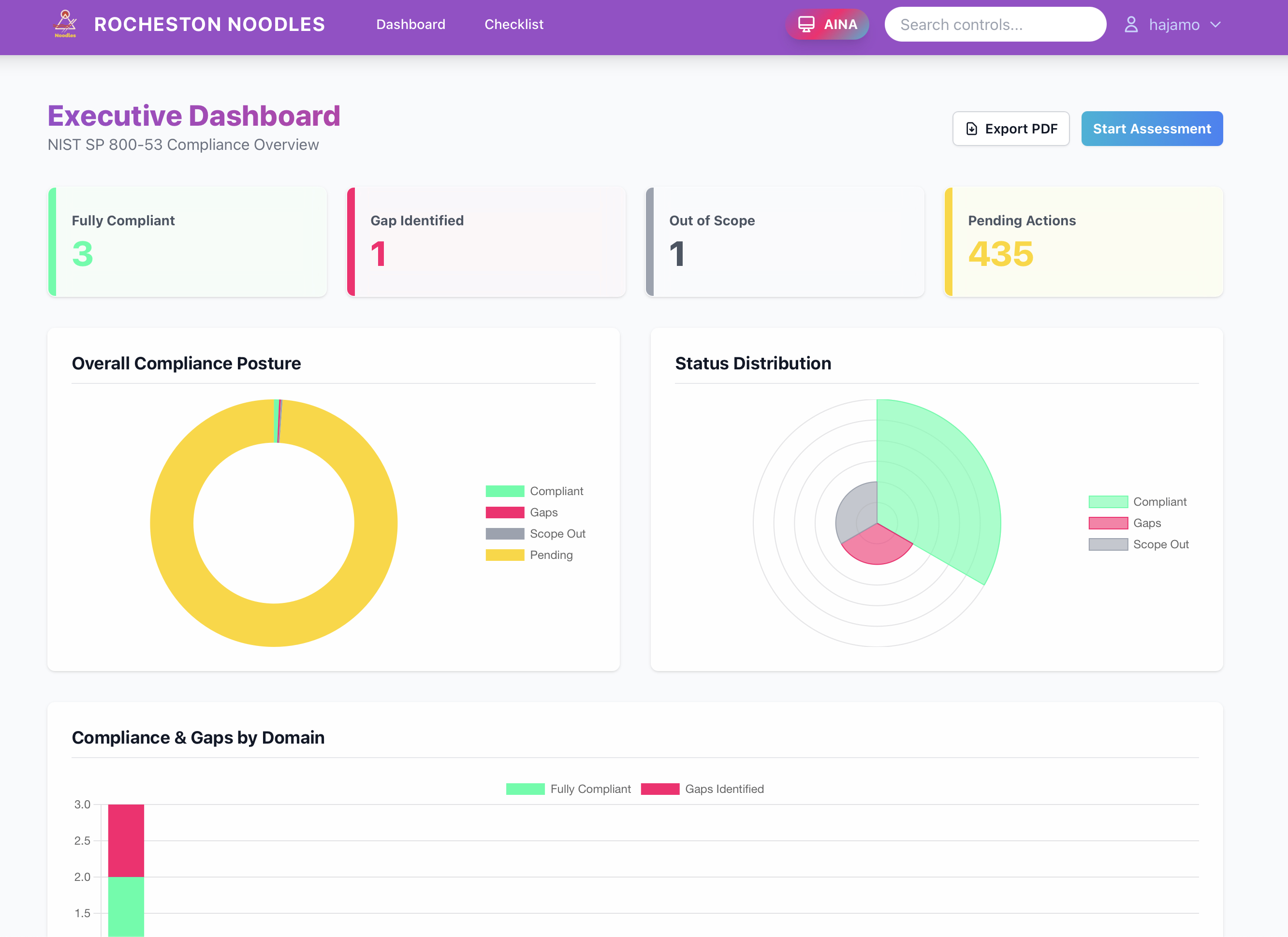
Managing 25 domains and more than 2,000 controls requires more than documentation. RCF is operationalized through the Rocheston Noodles platform, powered by AINA, Rocheston’s proprietary AI engine.
⚡ Continuous Validation
AINA connects directly to live infrastructure—such as cloud environments and security telemetry—to validate control states technically. Configuration drift is detected as it happens, not months later during an audit.
⛓️ Rosecoin Vault
Evidence generated by AINA can be hashed and anchored to the Rosecoin Vault, creating an immutable, timestamped record of compliance and security posture that cannot be silently altered.

The Five Strategic Tiers of RCF
🏗️ Tier 1: Governance and Foundation
- D1 Governance: Smart policy automation
- D2 Risk: Financial risk modeling
- D3 Supply Chain: Vendor provenance
- D4 Identity: Phishing-resistant MFA
- D5 Privacy: Sovereign data residency
💻 Tier 2: Technology and Infrastructure
- D6 AI Security: Model integrity & governance
- D7 Network: Zero trust architecture
- D8 Endpoint: Total asset visibility
- D9 SSDLC: Secure code & SBOM
📡 Tier 3: Operations and Defense
- D10 Monitoring: AI-driven SOC
- D11 Threat Intel: Active adversary tracking
- D12 VM: Continuous scanning
- D13 Incident Response: Automated playbooks
- D14 Resilience: Bunker protocols
- D15 Forensics: Cloud archaeology
🛡️ Tier 4: Future and Advanced Resilience
- D16 Post-Quantum: Future-proof crypto
- D17 Autonomous: Self-healing systems
- D18 Culture: The human firewall
- D19 Maturity: Continuous improvement
- D20 Evidence: Rosecoin Vault provenance
🚀 Tier 5: The Frontier
- D21 AI Agents: Bot economy defense
- D22 Space: Orbital security
- D23 Green Cyber: Sustainable operations
- D24 Neuro-Cognitive: Mind defense
- D25 Meta-Governance: Self-correction
One Framework. Many Obligations.
RCF reduces duplicated audits by harmonizing evidence once and reusing it across multiple standards and regulatory regimes.
✅ One Framework, Many Outcomes
RCF eliminates audit fatigue by design. By meeting the higher RCF baseline, organizations naturally cover requirements across multiple regulatory and assurance frameworks.
This means:
- A single control library mapped to many standards
- A single evidence pipeline reused across audits
- A single maturity score leadership can track over time
- A single operating model that remains valid as threats evolve
RCF makes compliance survivable—and then goes further.
🔮 Addressing Emerging Risks
RCF addresses risks that many frameworks still treat as optional or future concerns.
- Governance for autonomous AI agents
- Structured migration to quantum-safe cryptography
- Long-term evidence defensibility and provenance
- Human cognitive attack surfaces and resilience
- Frontier connectivity risks where applicable
Legacy standards provide a baseline. RCF provides survivability.

A Superset of Global Compliance Standards
RCF is engineered as a superset of leading global cybersecurity and assurance frameworks. Organizations that meet RCF requirements inherently satisfy the intent and technical safeguards of widely adopted standards such as NIST SP 800-53, ISO/IEC 27001, SOC 2, HIPAA, and PCI DSS.
Instead of managing each framework in isolation, RCF harmonizes overlapping requirements into a single, higher baseline. This allows organizations to implement once, reuse evidence across audits, and reduce multi-audit fatigue without sacrificing rigor.
Legacy frameworks were designed for static infrastructure and annual assessments. RCF is designed for environments that change continuously.
Future-First by Architecture
RCF integrates security domains that traditional standards only partially address—or do not address at all—into a single cohesive operating model.
This includes post-quantum cryptography planning, autonomous AI governance, continuous validation, and proof-grade evidence provenance. These capabilities are not bolt-ons. They are native to the framework.
RCF does not ask you to prove compliance once a year. It enables you to prove resilience every day.
Compliance You Can Prove.
RCF is built around measurable control states and traceable evidence—so compliance is defensible, not assumed.
The RCF Green Seal
The RCF Green Seal represents cybersecurity hygiene done right—security that stays healthy over time, not security that spikes once for an audit.
The green circle represents a protected environment: systems, identities, data, and operations in a monitored, resilient loop.
The two leaves symbolize a dual promise:
- Disciplined cyber hygiene through strong fundamentals
- Continuous renewal through verification, drift correction, and improvement
“RCF Compliant” signifies a proof-backed posture.
Level 5 represents top-tier maturity: continuously verified controls, effective governance, and future-ready resilience.
Deployed by Rocheston Cybersecurity Engineers (RCCE)
RCF is deployed by Rocheston Cybersecurity Engineers (RCCE), an elite group of practitioners trained to operate at the highest levels of modern security. These engineers specialize in securing complex networks, large-scale systems, and high-velocity environments where traditional security approaches fall short. Their expertise spans governance, architecture, automation, and continuous verification across the full RCF domain model.
RCCE engineers focus on real-world execution. They design resilient architectures, implement intelligent controls, connect evidence pipelines, and maintain security posture that adapts in real time. Their work goes beyond documentation and policy enforcement—RCCE engineers build systems that self-heal, withstand change, and continuously prove integrity in live production environments.
🚀 Engage RCCE Engineers to Implement RCF
Implementing RCF is not a documentation exercise—it is an architectural upgrade. Organizations engage Rocheston Cybersecurity Engineers (RCCE) to design, deploy, and operationalize RCF directly within their environments. RCCEs work alongside internal teams to assess scope, align systems, and implement controls that remain effective as infrastructure and threats evolve.
By engaging RCCE engineers, organizations accelerate adoption while reducing risk. Controls are implemented correctly, evidence pipelines are established from day one, and resilience is built into daily operations—not retrofitted for audits. The result is a security posture that is measurable, continuously verifiable, and aligned with multiple global compliance standards through a single, unified framework.
From Fragmented Compliance to Global Assurance.
RCF transforms disconnected standards and regulations into a single, continuously verifiable security posture.
