

Rocheston CE Standards
These standards outline the requirements and professional guidelines for individuals working in roles related to cybersecurity.
This CE document isn't just a routine list of guidelines, but a thorough 250-page guide derived from the commendable National Institute of Standards and Technology (NIST) framework 2.0.
The framework outlines the essential standards, procedures, and specifics that are fundamental to becoming proficient in the field of cybersecurity. This resourceful framework promises to be a valuable asset for both budding and professional cybersecurity engineers in improving their technical know-how.


RCCE Cybersecurity Framework
Rooted in the core objective of fostering a deep understanding of the multifaceted landscape of cyber threats and defenses, the RCF is the foundational blueprint for the Rocheston Certified Cybersecurity Engineer (RCCE) certification.
List of Domains:
- Network Security
- Application Security
- Endpoint Security
- Data Security
- Identity and Access Management (IAM)
- Cloud Security
- Mobile Security
- Internet of Things (IoT) Security
- Critical Infrastructure Security
- Incident Response
- Disaster Recovery and Business Continuity
- Threat Intelligence
- Penetration Testing and Vulnerability Assessment
- Blockchain Security
- Cryptography
- Forensics
- Governance, Risk, and Compliance (GRC)
- Security Awareness Training
- Zero Trust Architecture
- Cyber-Physical Systems Security
- Privacy
- Malware Analysis
- Cyber Insurance
- Embedded Systems Security
- Quantum Cryptography
- DevSecOps
- Artificial Intelligence and Machine Learning


NIST 2.0 Cybersecurity Framework
- The CE standards outline the requirements and professional guidelines for individuals working in roles related to cybersecurity.
- An essential aspect of these newly introduced standards is that they are fundamentally grounded in the NIST 2.0 framework. The National Institute of Standards and Technology's 2.0 framework is a comprehensive model recognized worldwide that is geared toward mitigating and managing cybersecurity risks.
- As Rocheston's CE standards utilize the NIST 2.0 framework as their foundation, they reflect the most up-to-date and effective strategies for dealing with cybersecurity threats and risk management.
- This new initiative by Rocheston signifies its commitment to reinforcing the security of digital platforms and the promotion of best practices in the field of cybersecurity.
Here is the CE Standard
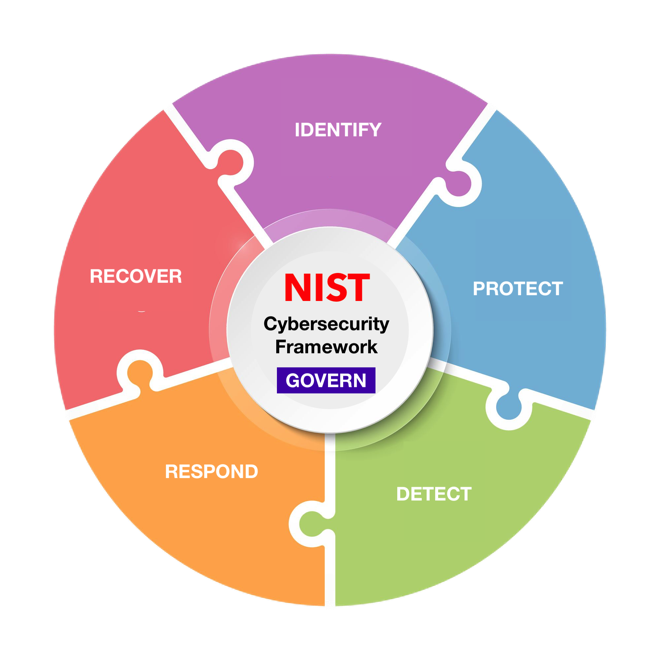
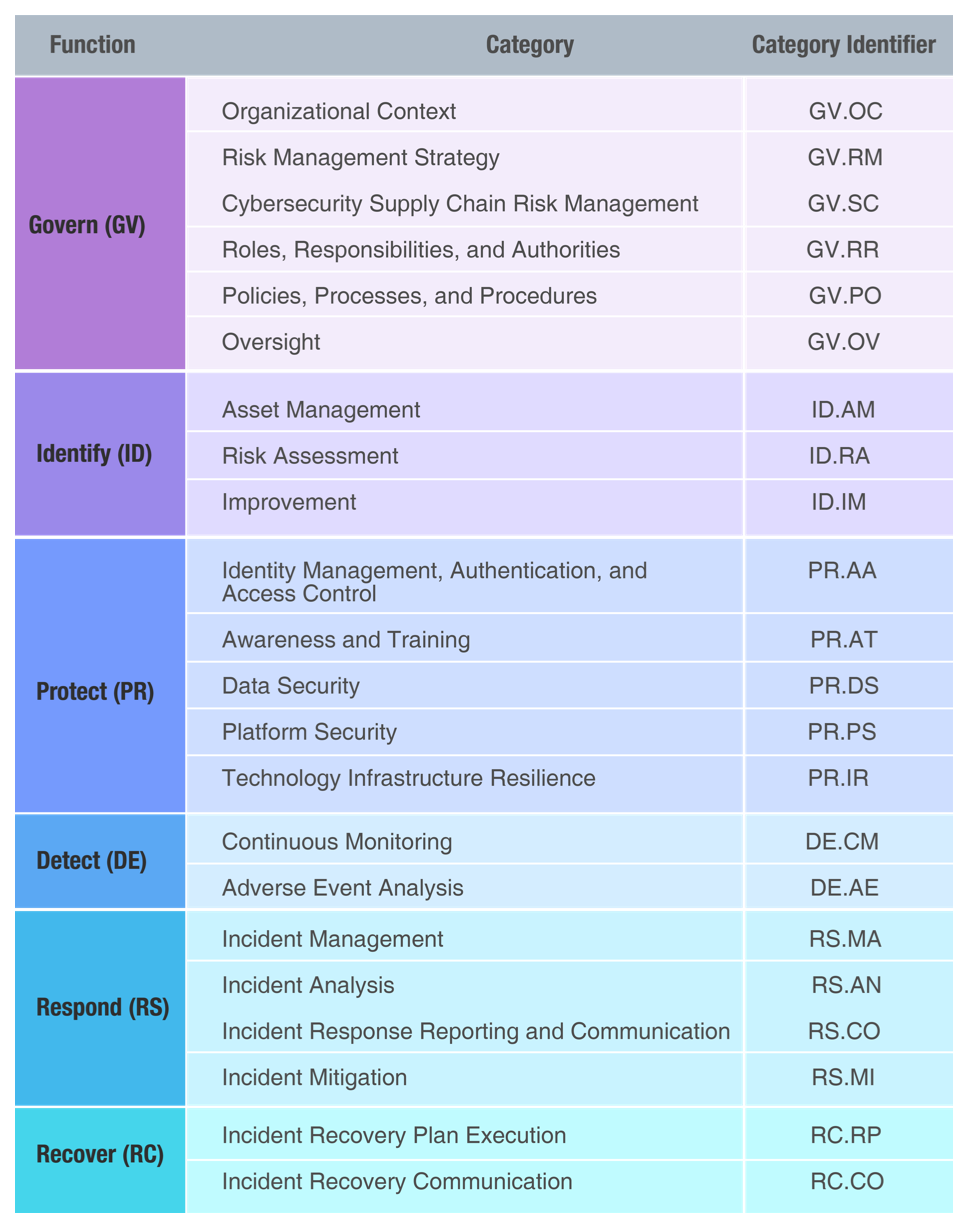
GOVERN – Establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy. The GOVERN Function is cross-cutting and provides outcomes to inform how an organization will achieve and prioritize the outcomes of the other five Functions in the context of its mission and stakeholder expectations. Governance activities are critical for incorporating cybersecurity into an organization’s broader enterprise risk management strategy. GOVERN directs an understanding of organizational context; the establishment of cybersecurity strategy and cybersecurity supply chain risk management; roles, responsibilities, and authorities; policies, processes, and procedures; and the oversight of cybersecurity strategy.
IDENTIFY – Help determine the current cybersecurity risk to the organization. Understanding its assets (e.g., data, hardware, software, systems, facilities, services, people) and the related cybersecurity risks enables an organization to focus and prioritize its efforts in a manner consistent with its risk management strategy and the mission needs identified under GOVERN. This Function also includes the identification of improvements needed for the organization’s policies, processes, procedures, and practices supporting cybersecurity risk management to inform efforts under all six Functions.
PROTECT – Use safeguards to prevent or reduce cybersecurity risk. Once assets and risks are identified and prioritized, PROTECT supports the ability to secure those assets to prevent or lower the likelihood and impact of adverse cybersecurity events. Outcomes covered by this Function include awareness and training; data security; identity management, authentication, and access control; platform security (i.e., securing the hardware, software, and services of physical and virtual platforms); and the resilience of technology infrastructure.
DETECT – Find and analyze possible cybersecurity attacks and compromises. DETECT enables timely discovery and analysis of anomalies, indicators of compromise, and other potentially adverse cybersecurity events that may indicate that cybersecurity attacks and incidents are occurring.
RESPOND – Take action regarding a detected cybersecurity incident. RESPOND supports the ability to contain the impact of cybersecurity incidents. Outcomes within this Function cover incident management, analysis, mitigation, reporting, and communication.
RECOVER – Restore assets and operations that were impacted by a cybersecurity incident. RECOVER supports timely restoration of normal operations to reduce the impact of cybersecurity incidents and enable appropriate communication during recovery efforts.
Organizational Context: The circumstances — mission, stakeholder expectations, and legal, regulatory, and contractual requirements — surrounding the organization’s cybersecurity risk management decisions are understood.
- The organizational mission is understood and informs cybersecurity risk management
- Internal and external stakeholders are determined, and their needs and expectations regarding cybersecurity risk management are understood
- Legal, regulatory, and contractual requirements regarding cybersecurity — including privacy and civil liberties obligations — are understood and managed
- Critical objectives, capabilities, and services that stakeholders depend on or expect from the organization are determined and communicated (formerly
- Outcomes, capabilities, and services that the organization depends on are determined and communicated
Risk Management Strategy: The organization’s priorities, constraints, risk tolerance and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions.
- Risk management objectives are established and agreed to by organizational stakeholders
- Risk appetite and risk tolerance statements are determined, communicated, and maintained
- Enterprise risk management processes include cybersecurity risk management activities and outcomes
- Strategic direction that describes appropriate risk response options is established and communicated
- Lines of communication across the organization are established for cybersecurity risks, including risks from suppliers and other third parties
- A standardized method for calculating, documenting, categorizing, and prioritizing cybersecurity risks is established and communicated
- Strategic opportunities (i.e., positive risks) are identified and included in organizational cybersecurity risk discussions
Cyber supply chain risk management processes are identified, established, managed, monitored, and improved by organizational stakeholders.
- A cybersecurity supply chain risk management program, strategy, objectives, policies, and processes are established and agreed to by organizational stakeholders
- Cybersecurity roles and responsibilities for suppliers, customers, and partners are established,
- communicated, and coordinated internally and externally
- Cybersecurity supply chain risk management is integrated into cybersecurity and enterprise risk management, risk assessment, and improvement processes
- Suppliers are known and prioritized by criticality
- Requirements to address cybersecurity risks in supply chains are established, prioritized, and integrated into contracts and other types of agreements with suppliers and other relevant third parties
- Planning and due diligence are performed to reduce risks before entering into formal supplier or other third-party relationships
- The risks posed by a supplier, their products and services, and other third parties are identified, recorded, prioritized, assessed, responded to, and monitored over the course of the relationship
- Relevant suppliers and other third parties are included in incident planning, response, and recovery activities
- Supply chain security practices are integrated into cybersecurity and enterprise risk management programs, and their performance is monitored throughout the technology product and service life cycle
- Cybersecurity supply chain risk management plans include provisions for activities that occur after the conclusion of a partnership or service agreement
Cybersecurity roles, responsibilities, and authorities to foster accountability, performance assessment, and continuous improvement are established and communicated.
- Organizational leadership is responsible and accountable for cybersecurity risk and fosters a culture that is risk-aware, ethical, and continually improving
- Roles, responsibilities, and authorities related to cybersecurity risk management are established, communicated, understood, and enforced
- Adequate resources are allocated commensurate with cybersecurity risk strategy, roles and responsibilities, and policies
- Cybersecurity is included in human resources practices
Organizational cybersecurity policies, processes, and procedures are established, communicated, and enforced.
- Policies, processes, and procedures for managing cybersecurity risks are established based on organizational context, cybersecurity strategy, and priorities and are communicated and enforced
- Policies, processes, and procedures for managing cybersecurity risks are reviewed, updated, communicated, and enforced to reflect changes in requirements, threats, technology, and organizational mission
Oversight: Results of organization-wide cybersecurity risk management activities and performance are used to inform, improve, and adjust the risk management strategy.
- Cybersecurity risk management strategy outcomes are reviewed to inform and adjust strategy and direction
- The cybersecurity risk management strategy is reviewed and adjusted to ensure coverage of
- organizational requirements and risks
- Organizational cybersecurity risk management performance is measured and reviewed to confirm and adjust strategic direction
Asset Management: Assets (e.g., data, hardware software, systems, facilities, services, people) that enable the organization to achieve business purposes are identified and managed consistent with their relative importance to organizational objectives and the organization’s risk strategy.
- Inventories of hardware managed by the organization are maintained
- Inventories of software, services, and systems managed by the organization are maintained
- Representations of the organization’s authorized network communication and internal and external network data flows are maintained
- Inventories of services provided by suppliers are maintaine
- Assets are prioritized based on classification, criticality, resources, and impact on the mission
- Inventories of data and corresponding metadata for designated data types are maintained
- Systems, hardware, software, and services are managed throughout their life cycle
Risk Assessment: The organization understands the cybersecurity risk to the organization, assets, and individuals.
- Vulnerabilities in assets are identified, validated, and recorded
- Cyber threat intelligence is received from information sharing forums and sources
- Internal and external threats to the organization are identified and recorded
- Potential impacts and likelihoods of threats exploiting vulnerabilities are identified and recorded
- Threats, vulnerabilities, likelihoods, and impacts are used to determine risk and inform risk prioritization
- Risk responses are chosen from the available options, prioritized, planned, tracked, and communicated
- Changes and exceptions are managed, assessed for risk impact, recorded, and tracked
- Processes for receiving, analyzing, and responding to vulnerability disclosures are established
- The authenticity and integrity of hardware and software are assessed prior to acquisition and use
Improvement: Improvements to organizational cybersecurity risk management processes, procedures and activities are identified across all Framework Functions.
- Continuous evaluation is applied to identify improvements
- Security tests and exercises, including those done in coordination with suppliers and relevant third parties, are conducted to identify improvements
- Lessons learned during execution of operational processes, procedures, and activities are used to identify improvements
- Cybersecurity plans that affect operations are communicated, maintained, and improved
Identity Management, Authentication, and Access Control: Access to physical and logical assets is limited to authorized users, services, and hardware, and is managed commensurate with the assessed risk of unauthorized access.
- Identities and credentials for authorized users, services, and hardware are managed by the organization
- Identities are proofed and bound to credentials based on the context of interactions
- Users, services, and hardware are authenticated
- Identity assertions are protected, conveyed, and verified
- Access permissions, entitlements, and authorizations are defined in a policy, managed, enforced, and reviewed, and incorporate the principles of least privilege and separation of duties
- Physical access to assets is managed, monitored, and enforced commensurate with risk
Awareness and Training: The organization’s personnel are provided cybersecurity awareness and training so they can perform their cybersecurity-related tasks.
- Users are provided awareness and training so they possess the knowledge and skills to perform general tasks with security risks in mind
- Individuals in specialized roles are provided awareness and training so they possess the knowledge and skills to perform relevant tasks with security risks in mind
Data Security: Data is managed consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information.
- The confidentiality, integrity, and availability of data-at-rest are protected
- The confidentiality, integrity, and availability of data-in-transit are protected
- Data is managed throughout its life cycle, including destruction
- The confidentiality, integrity, and availability of data-in-use are protected
- Backups of data are created, protected, maintained, and tested
Platform Security: The hardware, software (e.g., firmware, operating systems, applications), and services of physical and virtual platforms are managed consistent with the organization’s risk strategy to protect their confidentiality, integrity, and availability.
- Configuration management practices are applied
- Software is maintained, replaced, and removed commensurate with risk
- Hardware is maintained, replaced, and removed commensurate with risk
- Log records are generated and made available for continuous monitoring
- Installation and execution of unauthorized software are prevented
- Secure software development practices are integrated and their performance is monitored throughout the software development life cycle
Technology Infrastructure Resilience: Security architectures are managed with the organization’s risk strategy to protect asset confidentiality, integrity, and availability, and organizational resilience.
- Networks and environments are protected from unauthorized logical access and usage
- The organization’s technology assets are protected from environmental threats
- Mechanisms are implemented to achieve resilience requirements in normal and adverse situations
- Adequate resource capacity to ensure availability is maintained
Continuous Monitoring: Assets are monitored to find anomalies, indicators of compromise, and other potentially adverse events.
- Networks and network services are monitored to find potentially adverse events
- The physical environment is monitored to find potentially adverse events
- Personnel activity and technology usage are monitored to find potentially adverse events
- External service provider activities and services are monitored to find potentially adverse events
- Computing hardware and software, runtime environments, and their data are monitored to find potentially adverse events
Adverse Event Analysis: Anomalies, indicators of compromise, and other potentially adverse events are analyzed to characterize the events and detect cybersecurity incidents.
- Potentially adverse events are analyzed to better understand associated activities
- Information is correlated from multiple sources
- The estimated impact and scope of adverse events are determined
- Information on adverse events is provided to authorized staff and tools
- Cyber threat intelligence and other contextual information are integrated into the analysis
- Incidents are declared when adverse events meet the defined incident criteria
Incident Management: Responses to detected cybersecurity incidents are managed.
- The incident response plan is executed once an incident is declared in coordination with relevant third parties
- Incident reports are triaged and validated
- Incidents are categorized and prioritized
- Incidents are escalated or elevated as needed
- The criteria for initiating incident recovery are applied
Incident Analysis: Investigation is conducted to ensure effective response and support forensics and recovery activities.
- Analysis is performed to determine what has taken place during an incident and the root cause of the incident
- Actions performed during an investigation are recorded and the records’ integrity and provenance are preserved
- Incident data and metadata are collected, and their integrity and provenance are preserved
- The incident’s magnitude is estimated and validated
Incident Response Reporting and Communication: Response activities are coordinated with internal and external stakeholders as required by laws, regulations, or policies.
- Internal and external stakeholders are notified of incidents
- Information is shared with designated internal and external stakeholders
Incident Mitigation: Activities are performed to prevent expansion of an event and mitigate its effects.
- Incidents are contained
- Incidents are eradicated
Restore assets and operations that were impacted by a cybersecurity incident.
- The recovery portion of the incident response plan is executed once initiated from the incident response process
- Recovery actions are determined, scoped, prioritized, and performed
- The integrity of backups and other restoration assets is verified before using them for restoration
- Critical mission functions and cybersecurity risk management are considered to establish post- incident operational norms
- The integrity of restored assets is verified, systems and services are restored, and normal operating status is confirmed
- The criteria for determining the end of incident recovery are applied, and incident-related documentation is completed
Incident Recovery Communication: Restoration activities are coordinated with internal and external parties.
- Recovery activities and progress in restoring operational capabilities are communicated to designated internal and external stakeholders
- Public updates on incident recovery are properly shared using approved methods and messaging
How to Implement Cybersecurity Framework?
Implementing the National Institute of Standards and Technology (NIST) Cybersecurity Framework within an organization will require various strategic steps. Here is a detailed step-by-step guide on how to do it:
Step 1: Understanding the NIST Framework
The first step is to wisely comprehend the NIST framework. It is a set of best practices, guidelines, and standards that aid in managing cybersecurity-related risks. The main elements of the NIST framework are functions, categories, subcategories, and informative references. Being conversant with these elements will help streamline the implementation process.
Step 2: Assemble the Team
A successful implementation plan requires the input of a cross-functional team. The team should consist of the representative from various departments such as IT, human resources, operations, legal, and finance. This is because implementing the NIST framework is not just a technological step but also a business decision, hence involving all sectors is paramount.
Step 3: Establish Risk Management Policy
The organization should establish a comprehensive risk management policy outlining its risk appetite, tolerance, and strategies. This policy should be aligned with business objectives and should drive the implementation of the NIST Framework. Embedding cybersecurity in a band of organizational culture and policy can help assure ongoing attention and resources.
Step 4: Identify Systems, Assets, Data, and Capabilities
Make a comprehensive inventory and document all systems, software, data, and other capabilities associated with your IT infrastructure. Identify the critical systems and sensitive data that require special protection. This step is essential in understanding what you need to protect when a cyber threat occurs.
Step 5: Determine Current Risk Posture
Conduct a comprehensive risk assessment to determine the current cybersecurity risk posture of your organization. Understand your vulnerabilities, threats, and risks that your organization faces. This comprehensive risk assessment will serve as a baseline for implementing the NIST framework.
Step 6: Set Desired Outcomes
The NIST framework categorizes outcomes in sectors like protect, detect, respond, and recover. Setting these desired outcomes helps your team focus on what they should accomplish. This will also help in developing risk mitigation strategies.
Step 7: Develop an Implementation Plan
Use the current understanding of the cybersecurity risk and the desired outcomes to develop an action plan. The plan should outline how the organization will achieve the desired goals.
Step 8: Select Appropriate Security Controls
From the NIST special publication 800-53, which provides a list of security controls, choose those that align with your organization’s risk management strategy and compliance requirements.
Step 9: Implementation of Security Controls
Implement the selected security controls and monitor their ability to protect critical assets. This can involve configuring hardware and software, developing cybersecurity policies, and training.
Step 10: Continuous Monitoring
Implement a continuous monitoring strategy to ensure that security controls remain effective over time. Regular reviews and updates will help your organization remain adaptive to emerging cyber threats.
Step 11: Communicate
Communication is crucial in this process. All stakeholders should be informed about the implementations, challenges, and successes. This helps to ensure everyone understands the importance of cybersecurity and their roles in maintaining it.
Step 12: Review and Improve
Periodically review and evaluate the effectiveness of the implementation to ensure its alignment with the business objectives. Pinpoint areas for improvement and make adjustments where necessary.
Remember, implementing the NIST framework is hence not a one-time process but rather an ongoing one that requires continuous adaptation and improvement.
