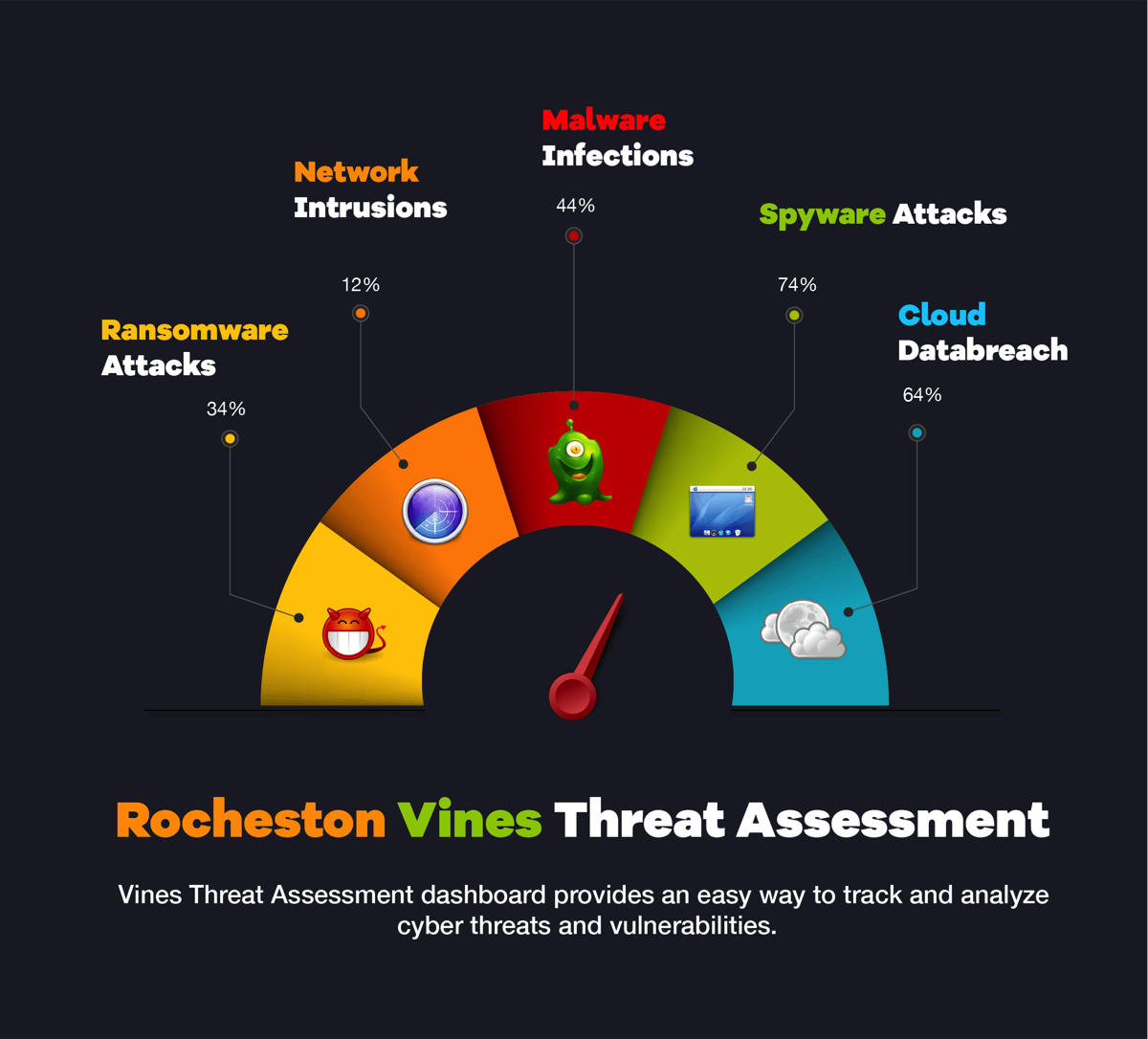
RCCE Level 2 Penetration Testing
This course stands out for its extensive coverage of advanced penetrating testing techniques.


Part 1
Cyber Range Exercises
- Gain real-world experience in identifying and exploiting vulnerabilities
- Understand how attackers think and strategize
- Develop the ability to prioritize and remediate vulnerabilities effectively
- Enhance their problem-solving and critical thinking skills
Rocheston Sphere Platform
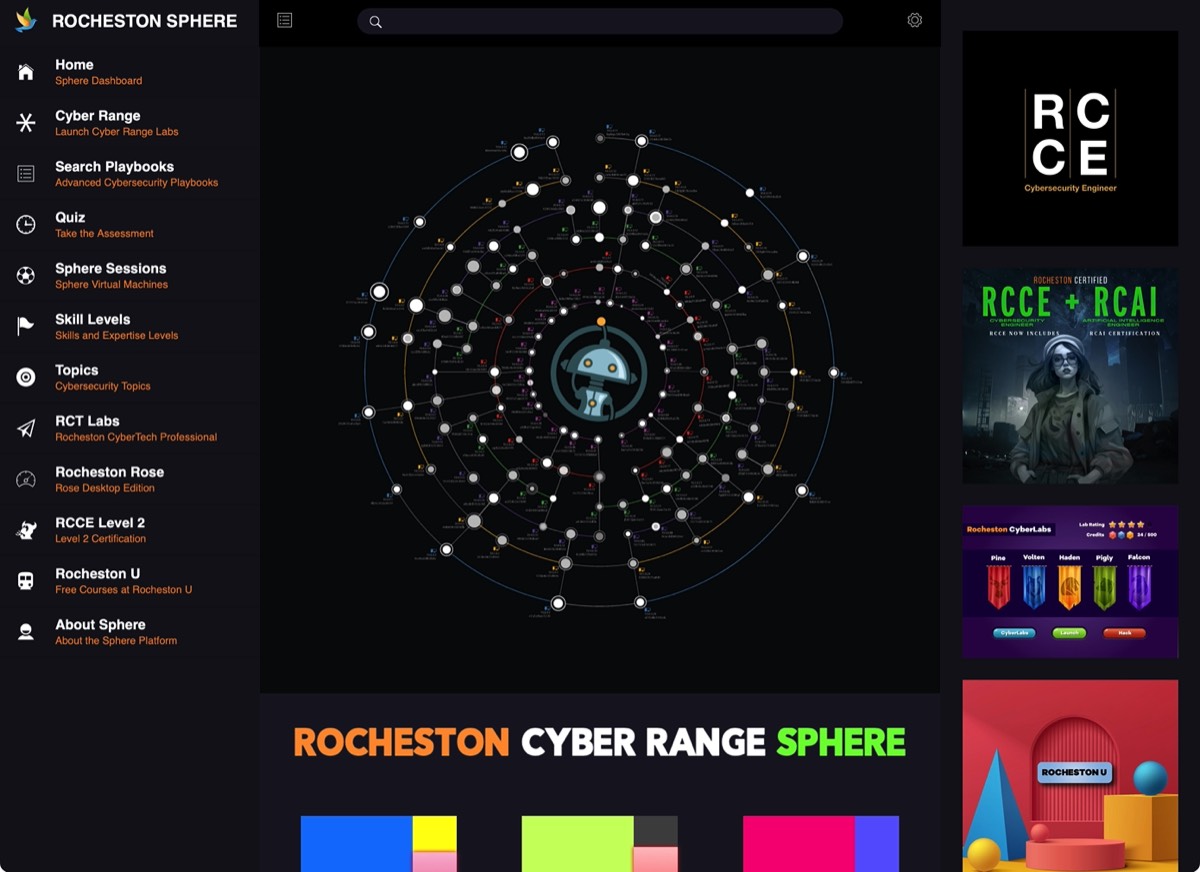
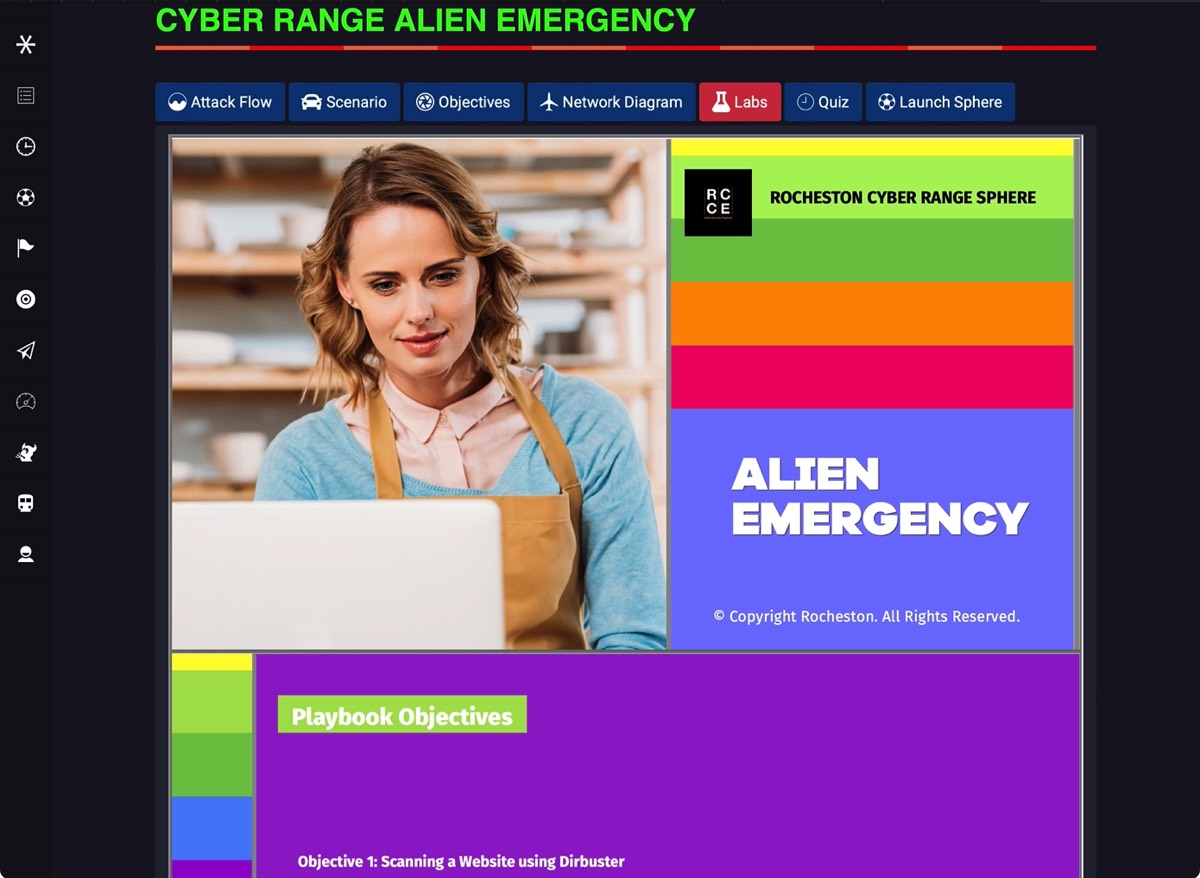
Sphere Playbooks
Employing advanced technology and providing immersive user experiences, Sphere stands as a benchmark by offering real-life scale cyber attack simulations, unmatched in its industry segment.








What is RCPT?
The RCCE Level 2 program, incorporating RCPT, aims to equip participants with an in-depth understanding of offensive and defensive cybersecurity strategies. The RCPT certification, in particular, has a strong emphasis on practical penetration testing techniques and methodologies.






RCPT Course Outline
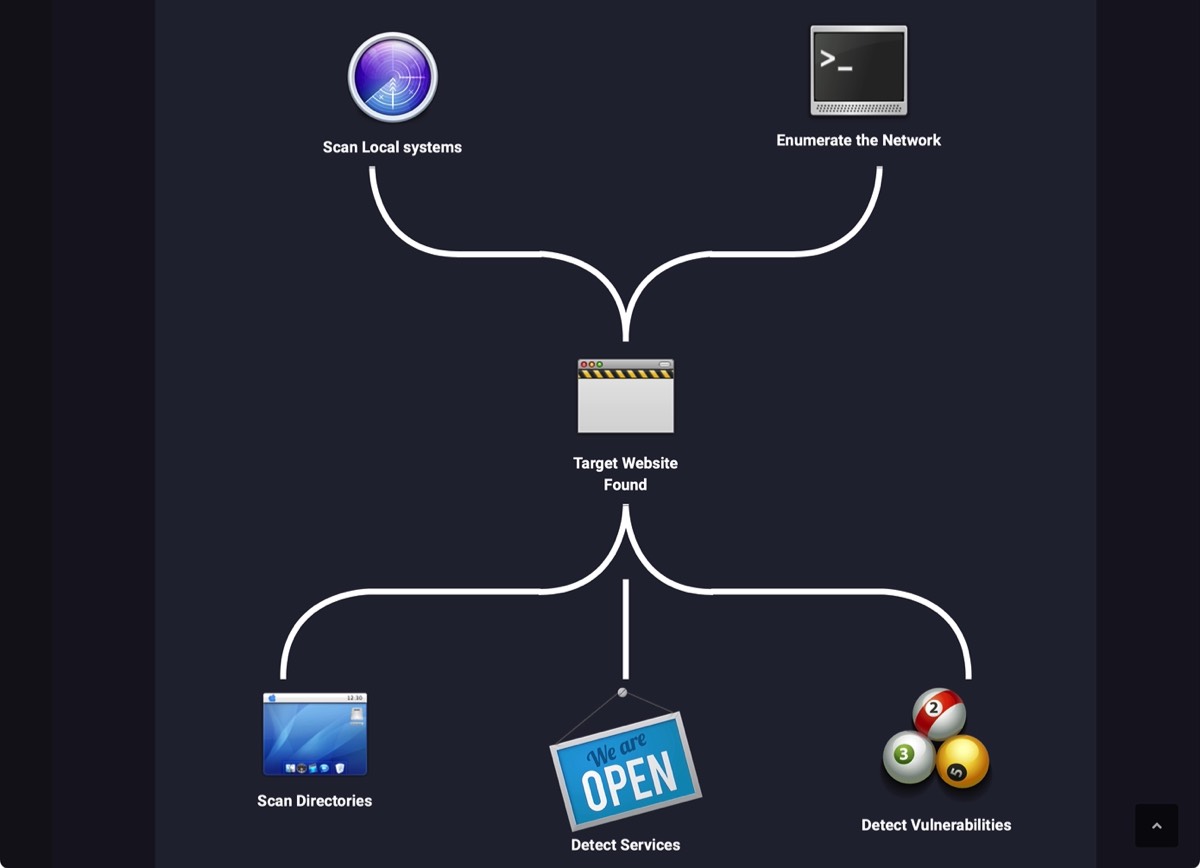
Scan Open Ports: Analyze open ports on the network.
Version Detection: Understand the versions of web servers, operating systems any outward-facing software by network footprinting.
Network Mapping: Use tools like Nmap to create a map of the network.
Vulnerability Analysis: Perform a vulnerability analysis to identify potential points of exploitation.
Firewall Configuration Testing: Checking the robustness of firewall rules and identifying misconfigurations.
Intrusion Detection/Prevention System Testing: Evaluate the effectiveness of IDS/IPS.
Password Strength Testing: Test the complexity and strength of passwords.
Password Cracking: Use password cracking tools to identify weak and easily crack-able passwords.
Brute Force Attacks: Try brute force attacks on login fields and other entry points.
Application Behavior: Understand the behavior of applications under varied user inputs.
Input Validation: Testing for weaknesses in input validation, such as cross-site scripting (XSS) or SQL injection vulnerabilities.
HTTP protocol verbs Testing: Test to see if unsupported or potentially risky HTTP protocol verbs are in use.
URL Manipulation: Manipulate URLs to bypass access controls or gain unauthorized access.
Cookie Security: Evaluate the security measures in place for cookies.
Session Management: Examine whether sessions are managed securely, including session timeouts and handling of concurrent logins.
Secure Token Testing: Confirm that secure tokens are used and are handled correctly.
Phishing Attack Simulation: Simulate phishing attacks to test response mechanisms and educate users.
Social Engineering: Use social engineering techniques to identify vulnerabilities in human factors.
Malware Testing: Test the protections against malicious software like viruses, worms, and Trojans.
Active Directory (AD) Testing: Evaluate the security of AD configurations.
Wi-fi Network Security: Assess the security of wireless networks and their configurations.
DDoS Mitigation Capability: Test the system's ability to sustain a Distributed Denial of Service (DDoS) attack.
DNS Security: Test the Domain Name System for cache poisoning or spoofing vulnerabilities.
Email Configuration: Check the email configurations to ensure security settings like SPF, DKIM, and DMARC are in place.
VoIP Testing: Voice over IP also needs to be tested for potential vulnerabilities.
SSL/TLS Testing: Check the implementation of cryptography, deprecated protocols, weak ciphers, and certificate validity.
Third-party Software: Any software from third parties or open-source libraries should be tested.
Intrusion Detection System (IDS): Test and evaluate its capacity to detect malicious traffic.
Intrusion Prevention System (IPS): Test and evaluate its capacity to prevent malicious traffic.
Patch Management Process: Evaluate how patches are managed and how quickly they're implemented.
Backup and Recovery Test: Validate the backup and recovery process of a company's data.
Physical Security Testing: Evaluate the effectiveness of physical security controls if relevant to the pen test.
Cloud Environment: Test security in cloud environments like AWS, Azure, or Google Cloud.
Database Security: Check for SQL injection, misconfigurations, and exposure of sensitive data in any database used.
Remote Access Testing: Assess the security of the Remote Desktop Protocol (RDP) or other remote access used.
Multi-factor authentication (MFA) Testing: Understand how MFA is implemented and identify any weaknesses.
File system permissions: Review file and directory permissions for any insecure settings.
Token Permissions: Review user and application tokens for unnecessary permissions.
Logs Auditing: Audit system, security and application logs to check for security incidents and anomalies.
Virtual Machine Security: Test the security of virtual machines if utilized.
Web Services/API Testing: Evaluate the security of any APIs or web services in use.
Mobile Application Testing: Testing mobile apps, if relevant, for any inherent vulnerabilities.
Unauthorized Data Access: Attempt to access sensitive or confidential data without appropriate permissions.
Administrative Interface Testing: Check for vulnerabilities in admin interfaces.
IoT Device Testing: Internet of Things devices, often overlooked, need proper pen testing too.
ARP Spoofing: Test for man-in-the-middle attack vulnerabilities.
VPN Security: Evaluate the security of Virtual Private Networks deployed in the organization.
Load balancer testing: Test to confirm it correctly handles network traffic and ensures data availability and redundancy.
Content Management System (CMS) Testing: Test the security of the CMS, a common target for attackers.
File Upload Testing: Check that file upload features sanitize input and reject potential malicious files.
Logic Testing: Make sure the application logic cannot be manipulated to achieve unauthorized access.
Session Hijacking: MethodInvocation and testing of session management to identify weaknesses.
DOS and DDOS: Test resilience against Denial of Service (DoS) or Distributed DoS attacks.
Business Logic Testing: Examine business processes to detect any logical or technical frailties.
Privilege Escalation: Try to gain higher permissions to access more resources.
Man-in-the-Middle (MITM) Attacks: Test vulnerabilities to MITM attacks.
Code Injection: Try injecting malicious code to exploit system or create unfavorable outcomes.
Information Disclosure: Test if internal system information disclosure happens through error messages.
Embedded Device Testing: If embedded or IoT devices are deployed, these need to also be pen tested.
Application Container Testing: Check the security of application container environments like Docker.
Infrastructure Configuration Review: Review security configurations of routers, switches, firewalls, etc.
Server Misconfigurations: Identify any server misconfigurations that could potentially expose the network.
Clickjacking: Test for vulnerabilities to clickjacking attacks.
Server Security Headers: Check for appropriate implementation of HTTP security headers.
Server-side Request Forgery (SSRF) Attacks: Test for vulnerabilities to SSRF attacks.
Race Condition Bugs: Test to detect potential race condition bugs in code execution.
Client-side Security Controls: Test all client-side security measures.
Cross-Site Request Forgery (CSRF) Attacks: Test for vulnerabilities to CSRF attacks.
OWASP Top 10 & other Standard Framework Testing: Test for vulnerabilities listed in the OWASP . Top 10 and other recognized security frameworks.
Insider Threat Simulation: Simulate actions of malicious insiders to identify vulnerabilities.
Human Interface Device (HID) Attacks: Test for potential HID attacks, such as BadUSB.
Regulatory Compliance Pen Testing: Specialized tests to ensure compliance with regulations such as PCI DSS, HIPAA, GDPR.
Spear Phishing: Test employee susceptibility to targeted spear phishing attacks.
Third Party and Supplier Security: Test security preparedness of third parties and supply chain elements.
Cloud Storage Security: Test the security of storage buckets like Amazon S3 or Azure Blob Storage.
Red Teaming: Conduct complete cyber-attack simulations to evaluate organization's defense capability.
Zero-day Exploit Testing: If zero-day exploits are discovered, understand their impact and mitigation.
Cloud Container Testing: Test the security of containers in cloud services.
Shadow IT Detection: Detect unmanaged systems or services within the network.
Breach Readiness Assessment: Understand the readiness of the organization to handle a breach.
Social Media Footprinting: Check for unintentionally revealed information on social media that could help attackers.
Security Policy Compliance: Test to ensure adherence to organization’s security policy.
Incident Response Capability: Test the organization's readiness to respond to security incidents.
Security Training Efficacy: Evaluate how effective the security awareness and training programs are within the organization.
Codebase Review: Manually review the codebase for any bugs or oversights that automated tools missed.
Security Tool Efficacy: Assess whether the security tools deployed by the organization are performing as expected.
Zero Trust Architecture Testing: Evaluate the effectiveness of zero trust models if implemented.
Local Network Access Control: Evaluate the controls in place for local network access.
Encryption At Rest & In Transit: Test for proper implementation of encryption both for data at rest and in transit.
Cyber Threat Intelligence Integration: Utilize cyber threat intelligence to add context and better identify potential threats.
Bot Detection: Test if the system has adequate protection against bots.
Email Phishing Campaigns: Test employees ability to recognize and avoid phishing scams.
Anti-Malware Efficacy: Test if the deployed antivirus or antimalware solution is effective.
Real-time Alerting: Test the incident alert mechanisms to ensure they are working properly.
Use of Known Vulnerabilities: Utilize known vulnerabilities from repositories like the Common
Vulnerabilities and Exposures (CVE) database.
Rogue Device Detection: Test the organization's ability to detect unauthorized devices on the network.
Pen Testing from Various Locations: Test the security measures from diverse geographical locations and IP addresses.
Threat Hunting: Proactively identify whether there are any unknown threats lurking in the infrastructure.
Ongoing Tests: Regular and scheduled penetration tests to account for new vulnerabilities and system changes.
Cyber Range VMs
-
Binary Bandit
-
Infobit Invader
-
Cypher Slayer
-
Data Drifter
-
Firewall Phantom
-
Ghost Protocol
-
Crypto Raider
-
Stealth Sentinel
-
Trojan Templar
-
Virtual Vandal
-
Packet Pirate
-
Quantum Quencher
-
Malware Marauder
-
Darknet Dynamo
-
Shellcode Samurai
-
Hexcode Havoc
-
Rootkit Rogue
-
Kernel Kraken
-
Logic Bombardier
-
Zero-Day Zephyr
-
Exploit Exterminator
-
DDoS Destroyer
-
Cyber Cipher
-
Port Prowler
-
Web Wormhole
-
SQL Sniper
-
Phishing Phantom
-
Ransomware Reaper
-
Keylogger Kingpin
-
Cross-Site Crusader
-
Algorithm Assassin
-
Debug Dragoon
-
Session Hijacker
-
Botnet Butcher
-
Network Ninja
-
Virus Vanquisher
Edit Category -
Spyware Slayer
-
Warez Warrior
-
Brute Force
-
Encoding Enigma
-
Protocol Punisher
-
Regex Renegade
-
Cookie Crasher
-
Code Injection
-
Firewall Fracturer
-
DoS Demolisher
-
Reverse Shell
-
Payload Plunderer
-
Socket Sorcerer
-
OAuth Outlaw
-
Bypass Buccaneer
RCCE® and Cybersecurity Engineer® are registered trademarks owned by Rocheston. All rights reserved.