

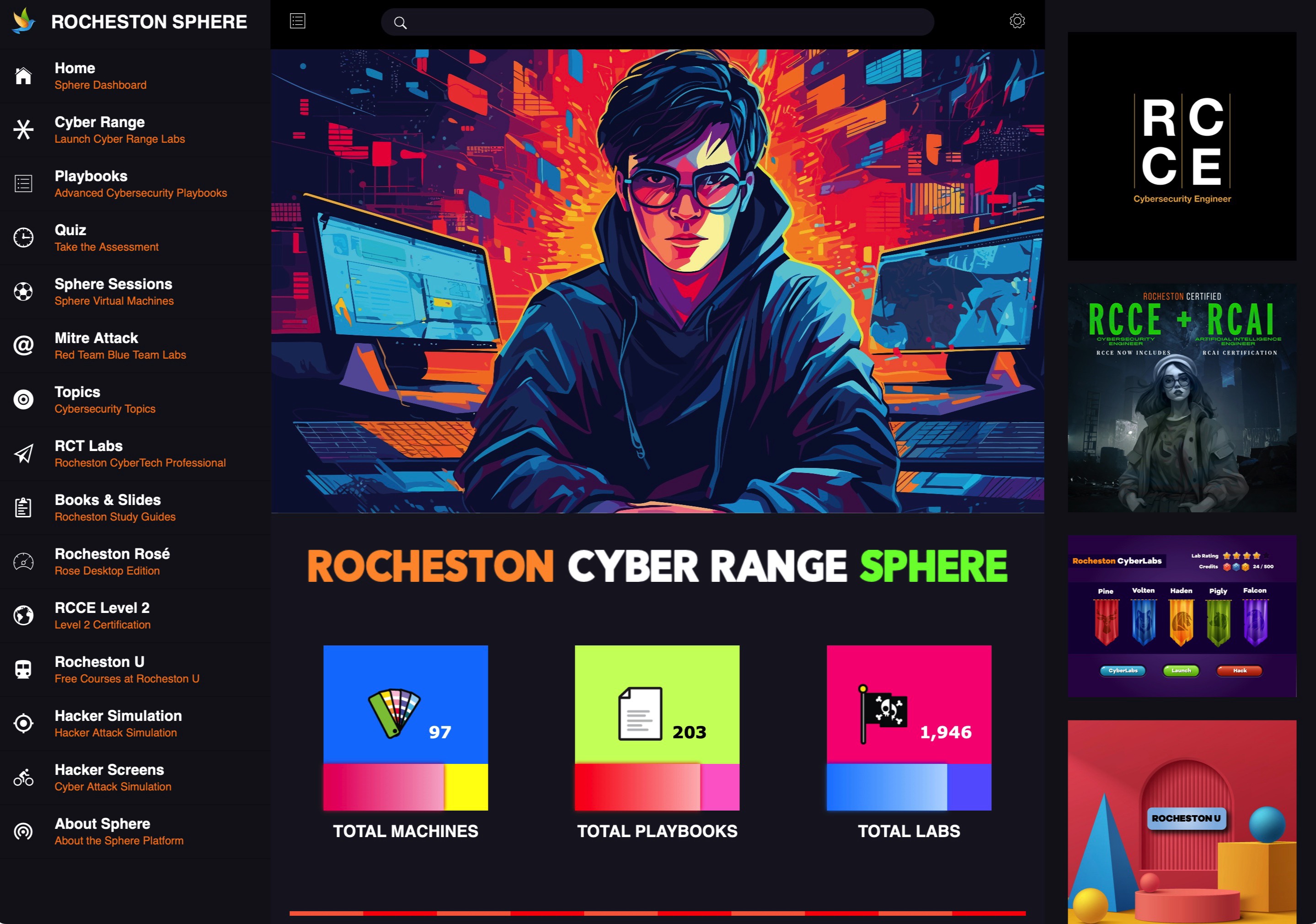
Rocheston Cyber Range Sphere
Sphere Platform
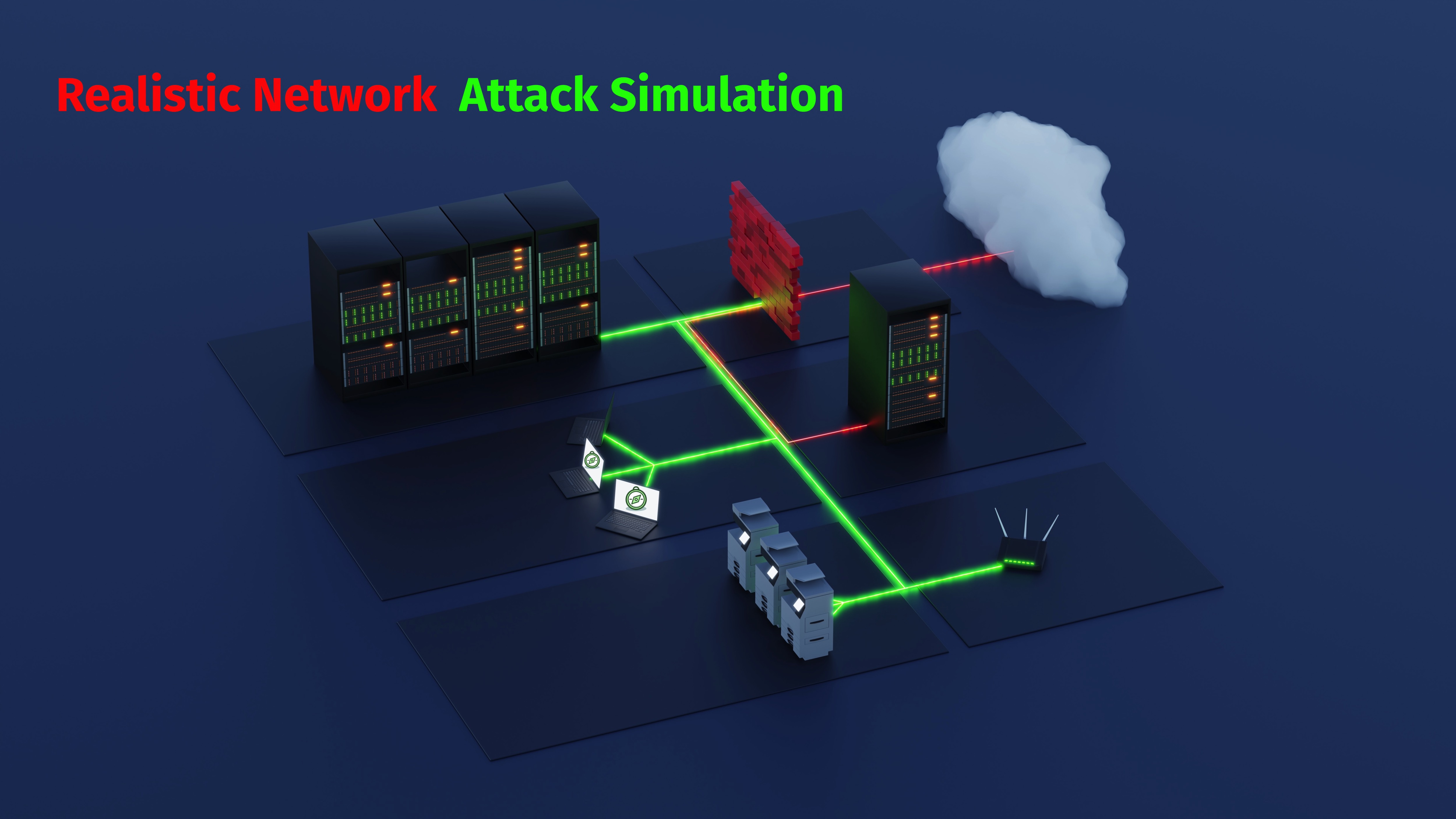
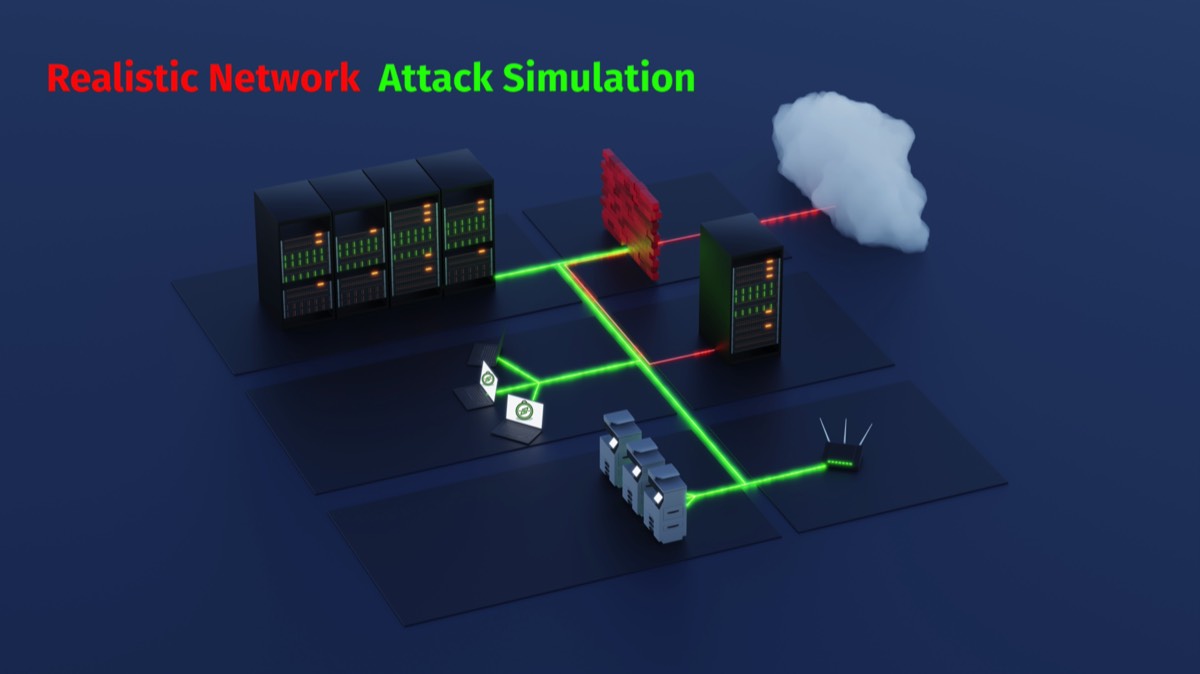
Developed with cutting-edge technology and a rich, immersive user experience, Sphere offers realistic cyber attack simulations on a scale that is unmatched in the market.

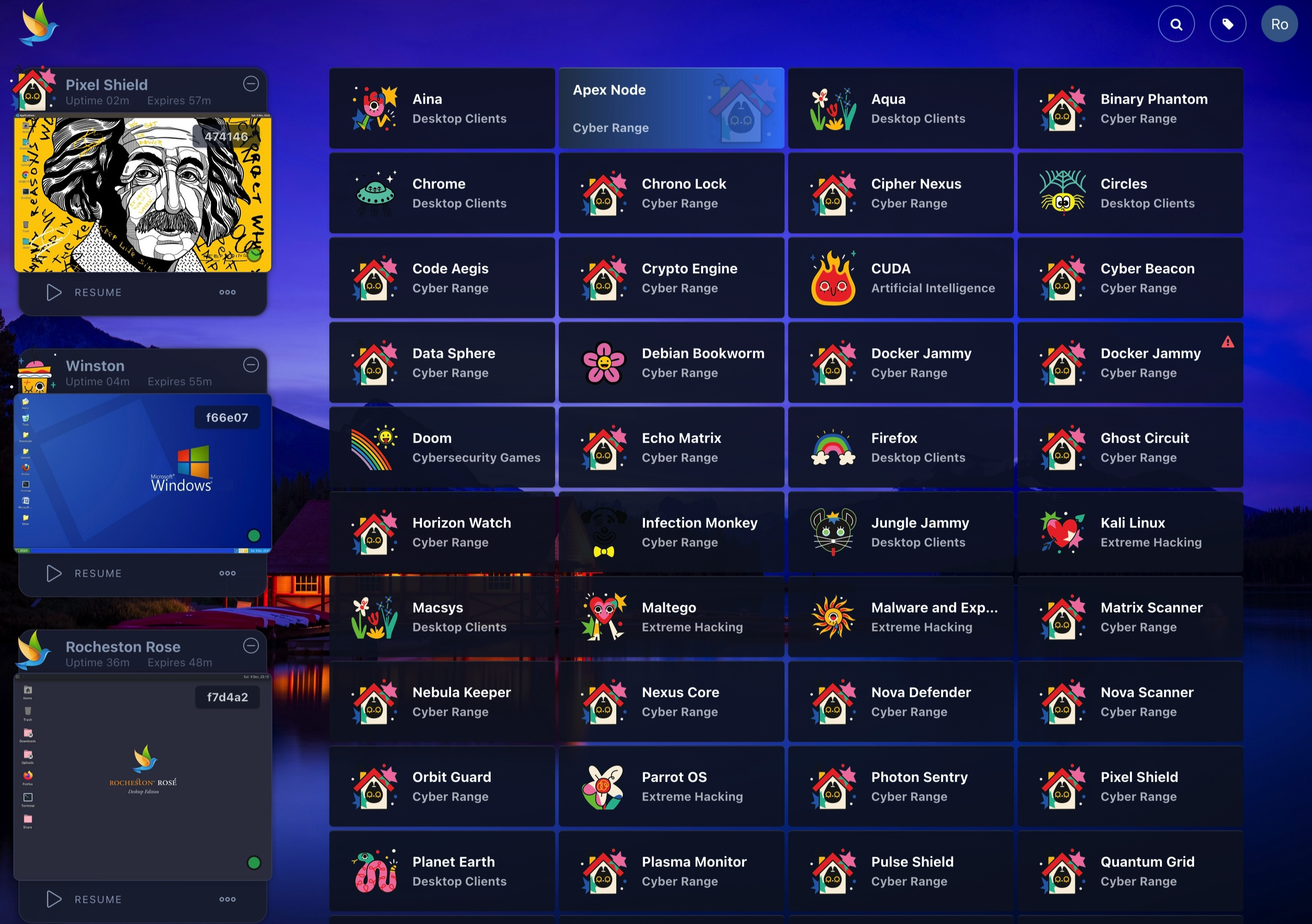
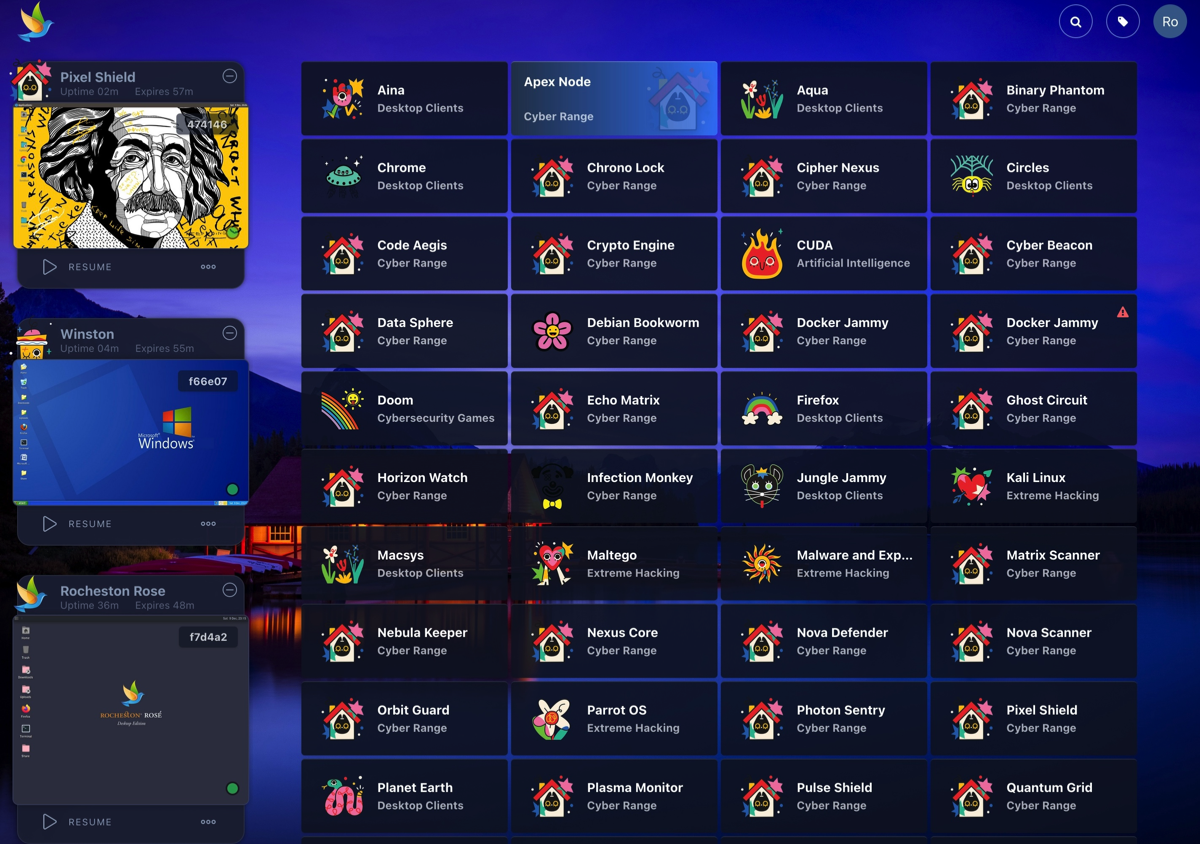
Cloud Hosted Labs

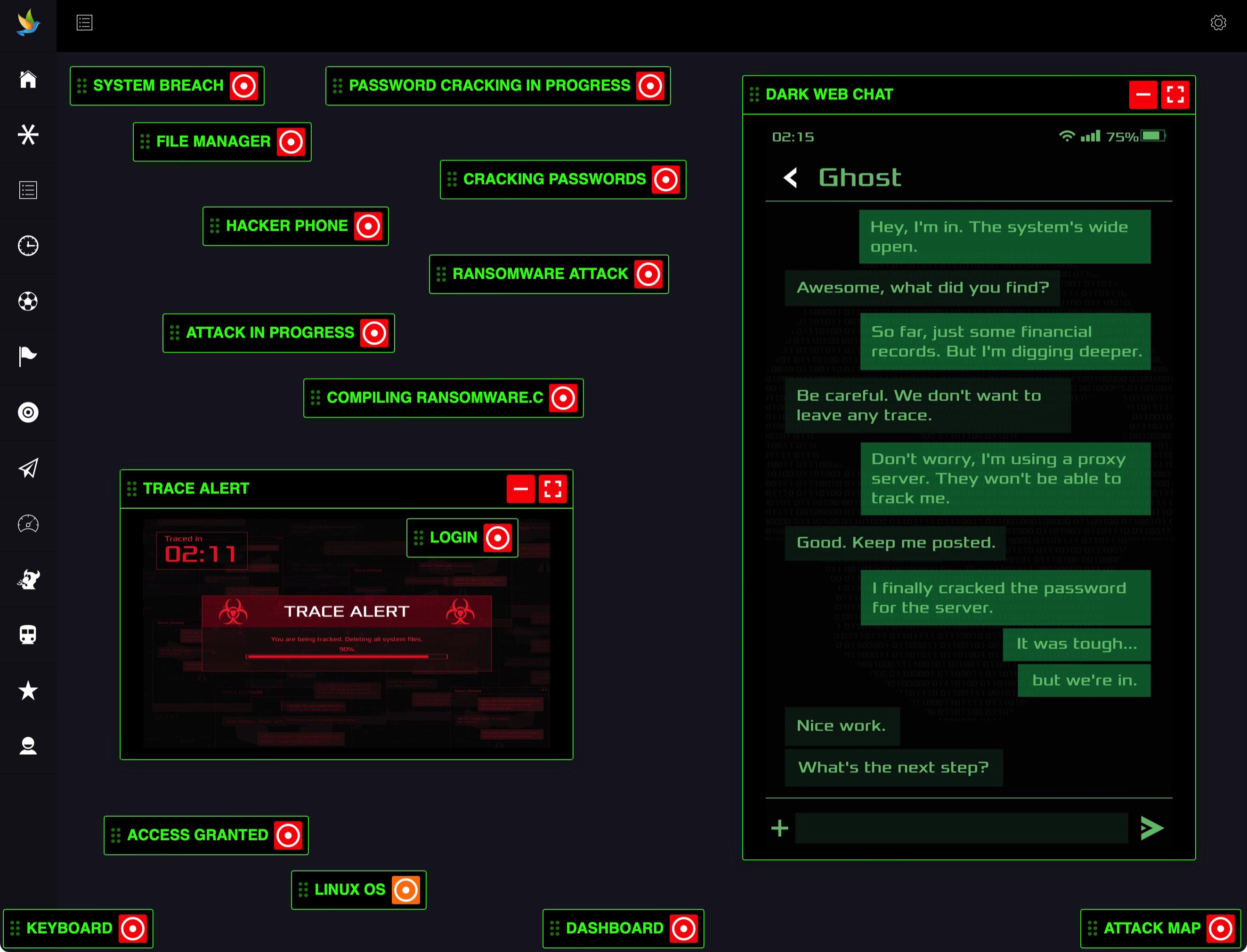
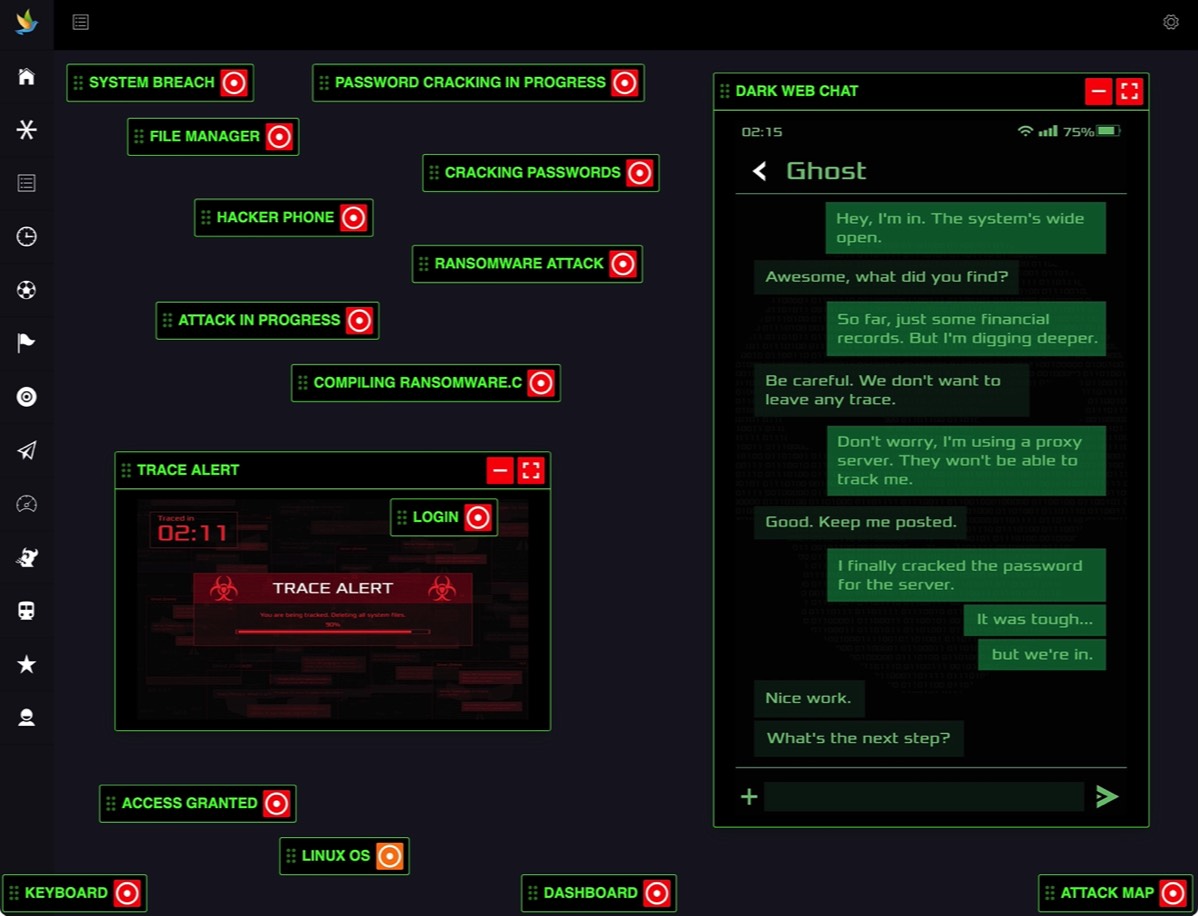

Thousands of Virtual Machines


Realistic Simulations

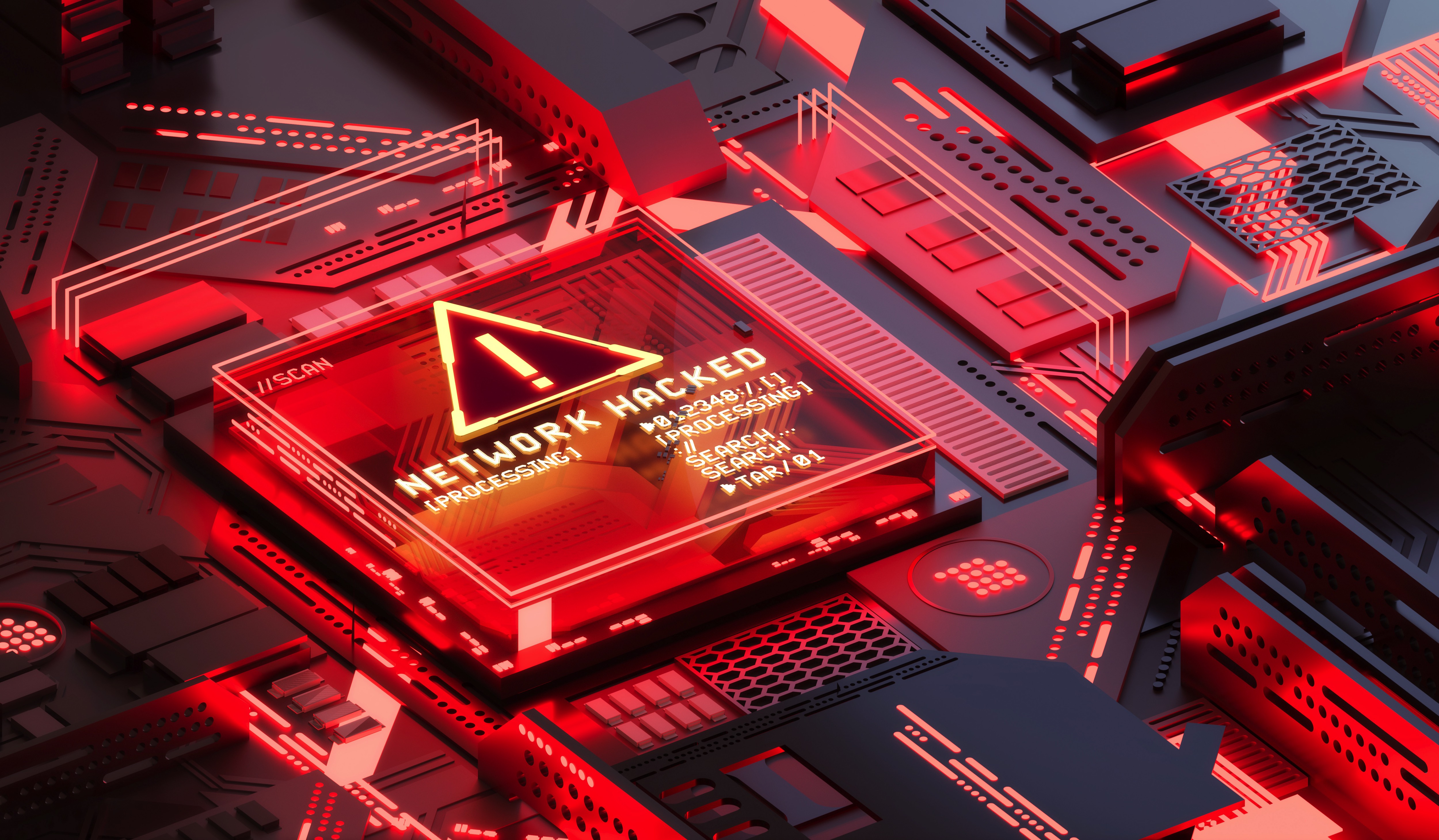

Counter Hacker Tactics

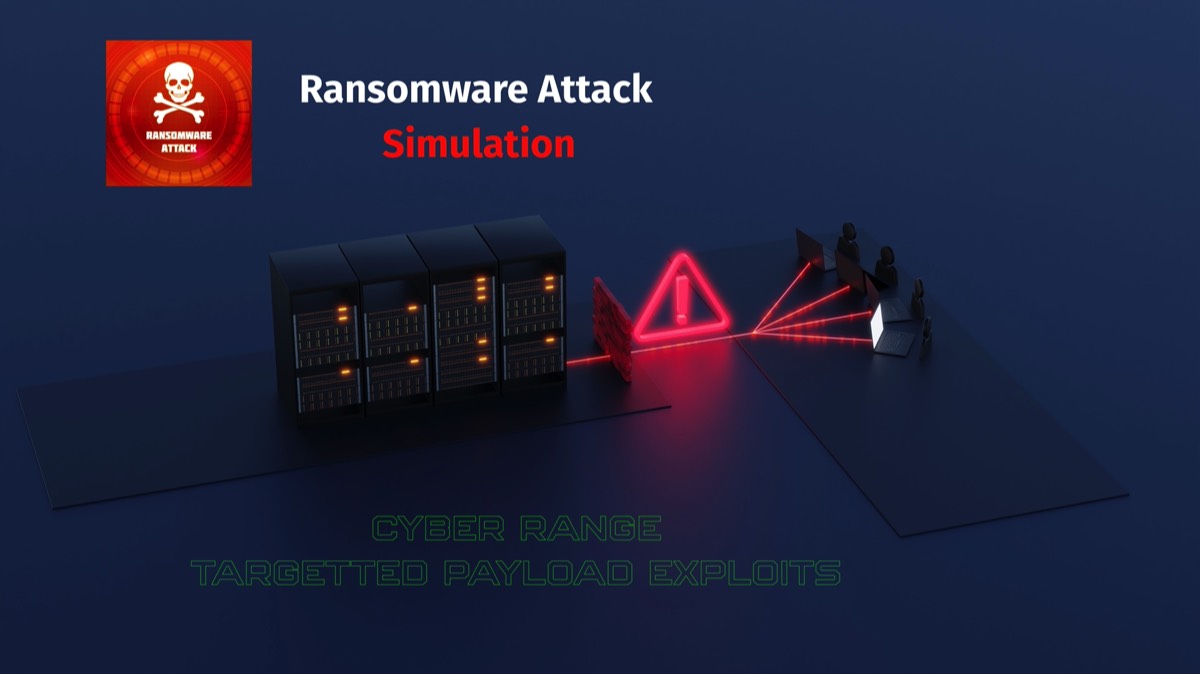


Advanced User Interface

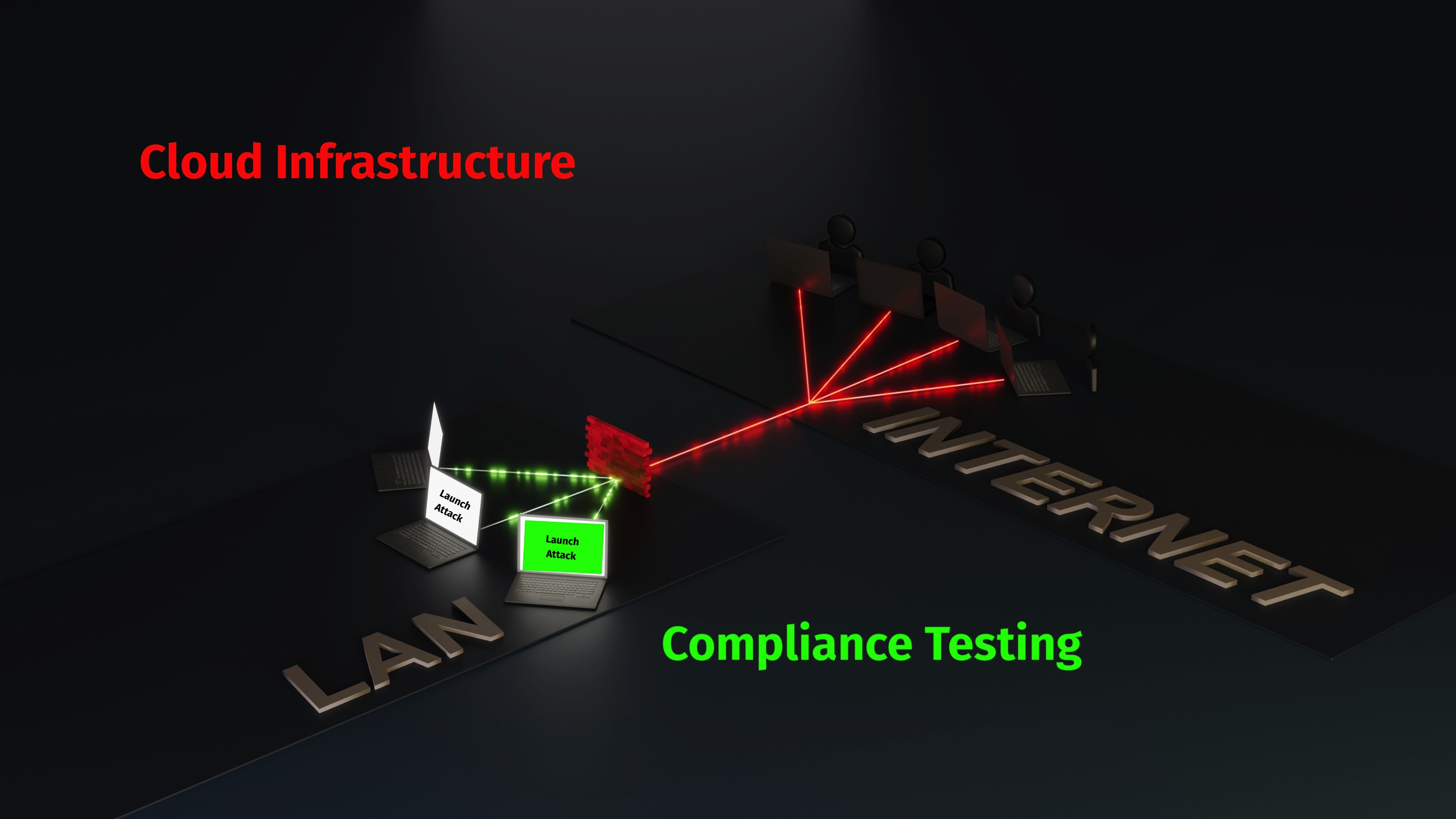

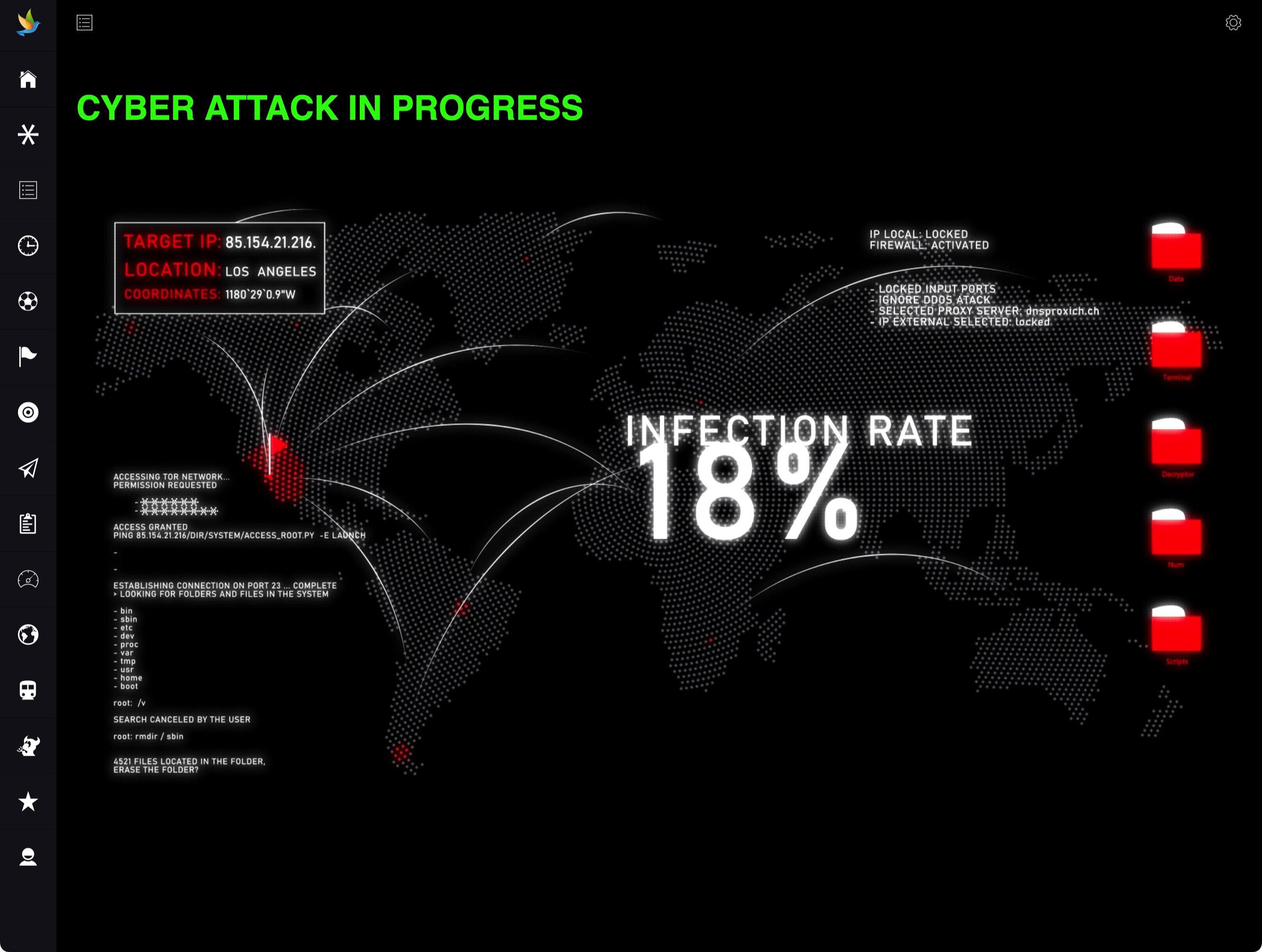
Real-time Dashboards


RCCE Level 2 Training



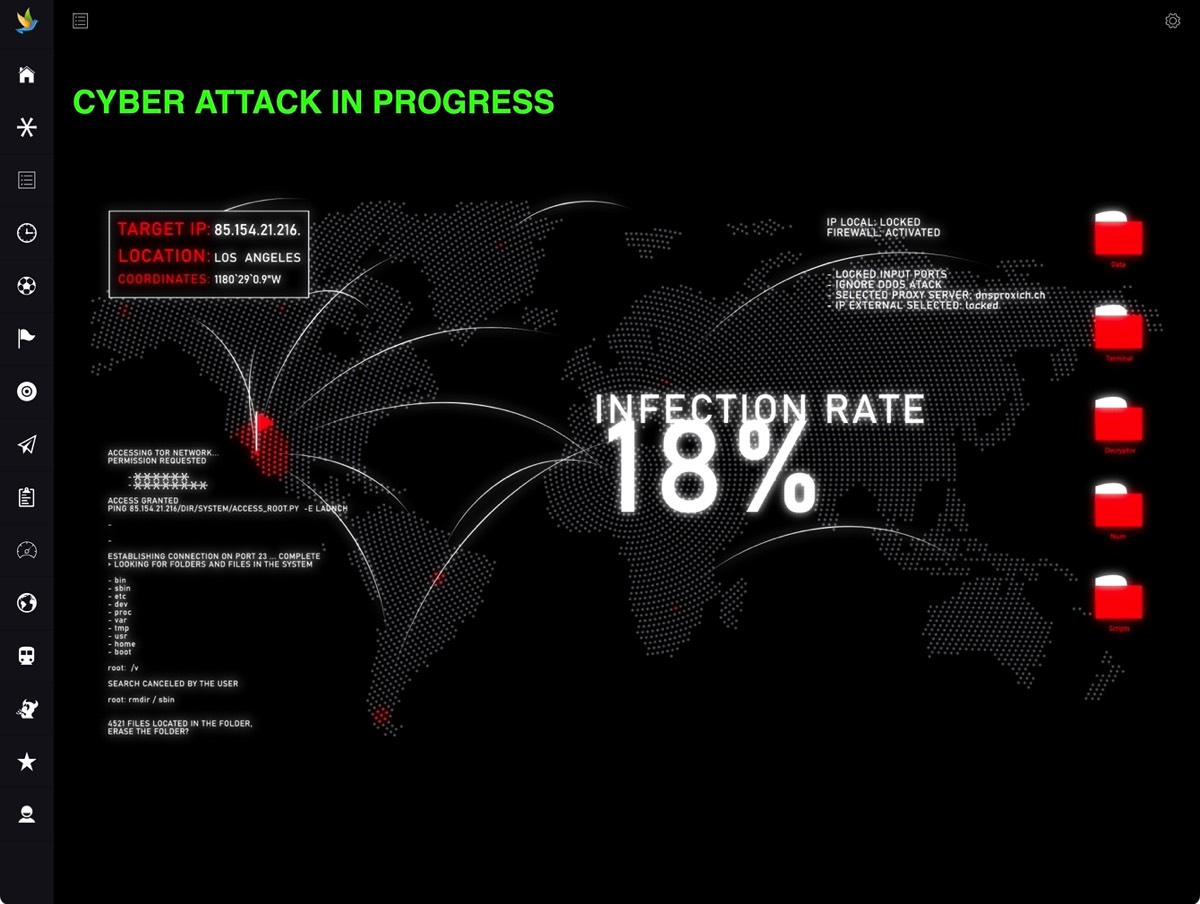

Exploration of the Digital Threat Landscape
Sophisticated Attack Playbooks

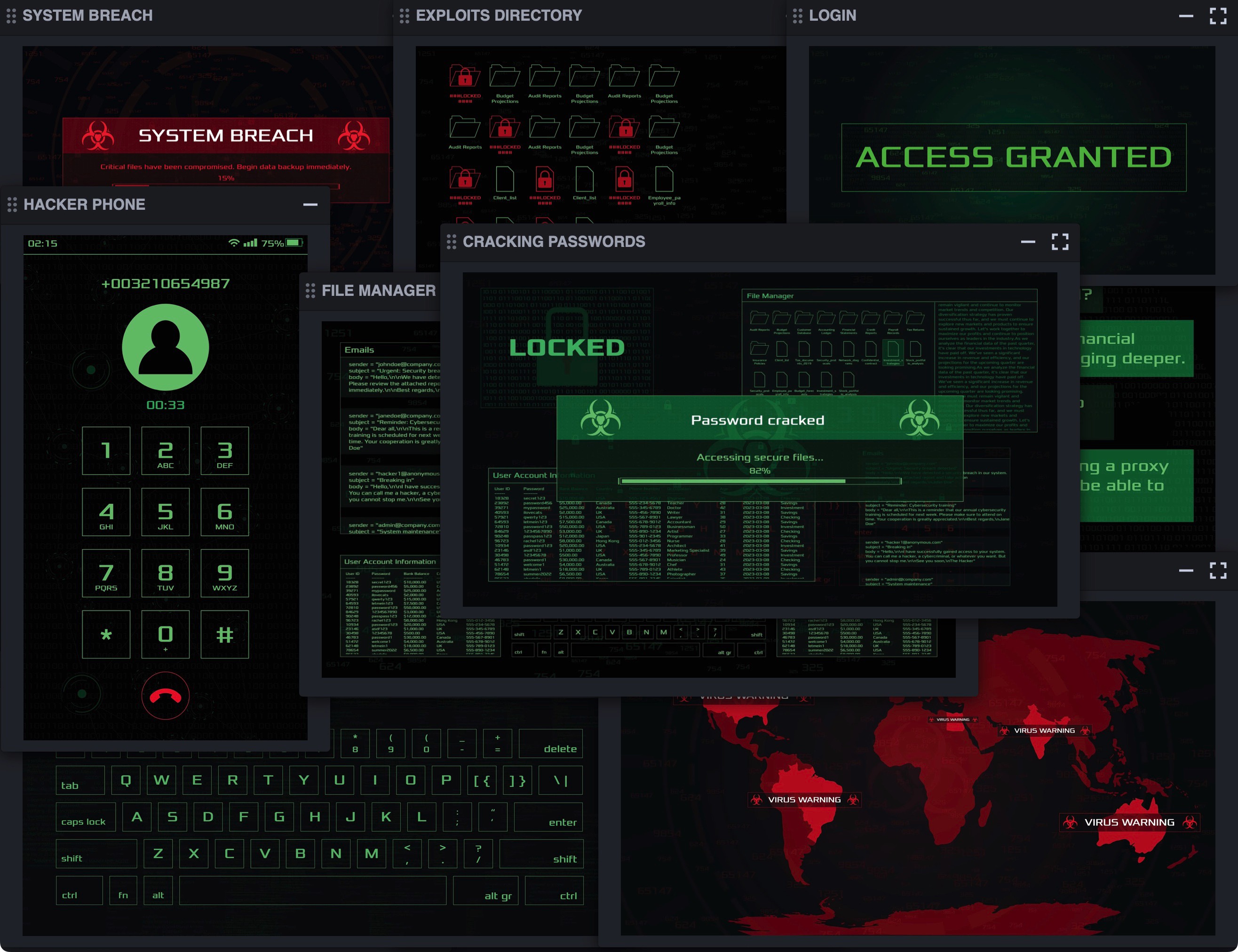

Sphere Playbooks
Ransomware Data Recovery and Continuity Planning Playbook |
|
|---|---|
Ransomware Payment and Negotiation Tactics Playbook |
|
|---|---|
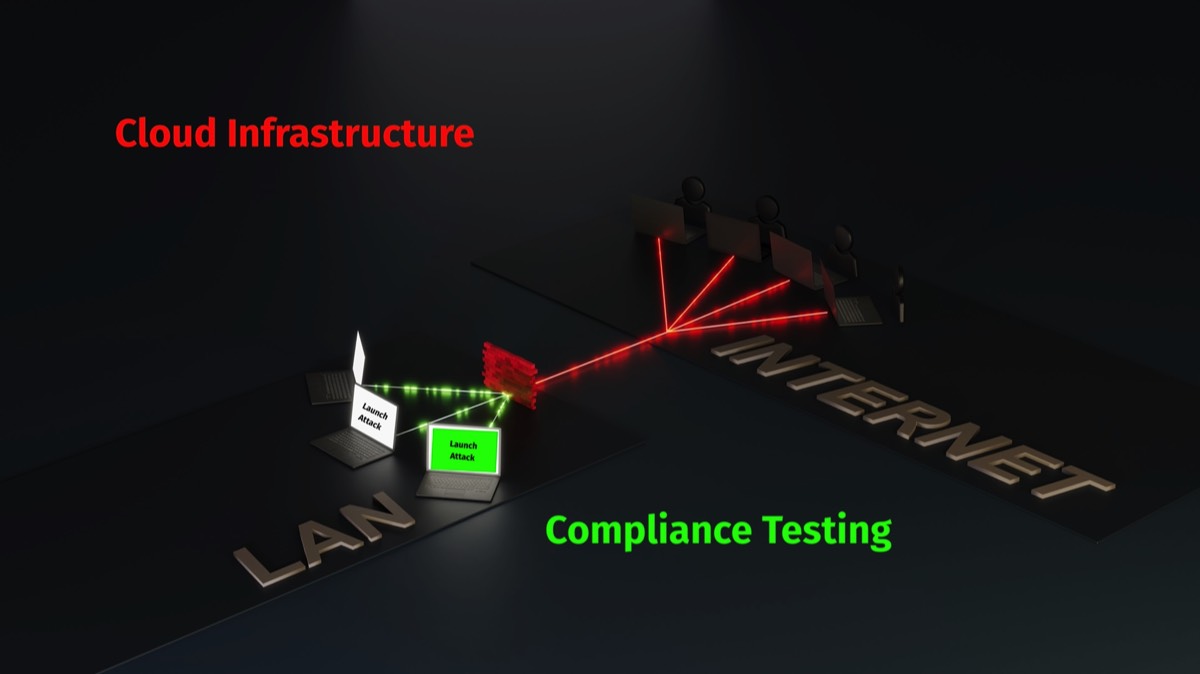
Cloud Infrastructure Compliance Auditing Playbook |
|
|---|---|
Application Micro-Segmentation in Zero Trust Playbook |
|
|---|---|
Incorporating DevSecOps into Legacy Systems Playbook |
|
|---|---|
Establishing a Cyber Threat Intelligence Program Playbook |
|
|---|---|
Endpoint Security with Advanced EDR/XDR Controls Playbook |
|
|---|---|
Ransomware Attack Vector Isolation Playbook |
|
|---|---|
Cloud Native Application Security Testing Playbook |
|
|---|---|
Enforcing Data-Centric Zero Trust Policies Playbook |
|
|---|---|
Spear Phishing Defense Playbook: Email Security Scenarios |
|
|---|---|
Next-Generation Firewall Deployment Playbook |
|
|---|---|
Zero-Day Exploit Containment Playbook |
|
|---|---|
Insider Threat Simulation and Management Playbook |
|
|---|---|
Network Segmentation and Access Control Playbook |
|
|---|---|
Cryptographic Attack Mitigation Playbook |
|
|---|---|
Web Application Penetration Testing Playbook |
|
|---|---|
Cloud Misconfiguration Discovery Playbook |
|
|---|---|
Secure DevOps Pipeline Creation Playbook |
|
|---|---|
Ransomware Attack Response and Recovery Playbook |
|
|---|---|
Data Exfiltration Prevention Techniques Playbook |
|
|---|---|
Incident Response Team Coordination Playbook |
|
|---|---|
Endpoint Detection and Response Tactics Playbook |
|
|---|---|
Forensic Analysis and Evidence Preservation Playbook |
|
|---|---|
Distributed Denial of Service (DDoS) Defense Playbook |
|
|---|---|
Compliance and Regulatory Framework Assessment Playbook |
|
|---|---|
Advanced SQL Injection Defense Playbook |
|
|---|---|
Malware Analysis and Reverse Engineering Playbook |
|
|---|---|
Multi-Factor Authentication Implementation Playbook |
|
|---|---|
Identity Access Mismanagement Incident Playbook |
|
|---|---|
Cyber Threat Hunting Techniques Playbook |
|
|---|---|
Rootkit Detection and Eradication Playbook |
|
|---|---|
Secure Code Review and Improvement Playbook |
|
|---|---|
Server Hardening and Security Baseline Playbook |
|
|---|---|
Supply Chain Attack Simulation Playbook |
|
|---|---|
Privileged User Escalation Prevention Playbook |
|
|---|---|
Security Information and Event Management (SIEM) Integration Playbook |
|
|---|---|
Botnet Infiltration and Disruption Playbook |
|
|---|---|
Cybersecurity Policy Development and Execution Playbook |
|
|---|---|
Mitre-Attack Framework Red Team Challenge Playbook |
|
|---|---|
Business Email Compromise (BEC) Countermeasures Playbook |
|
|---|---|
Advanced Persistent Defense Simulation Playbook |
|
|---|---|
Container Security Orchestration Playbook |
|
|---|---|
Cyber Range Blue Team Defensive Playbook |
|
|---|---|
Phishing Site Take Down Operation Playbook |
|
|---|---|
Incident Command System Deployment Playbook |
|
|---|---|
Credential Theft and Account Takeover Playbook |
|
|---|---|
Evasive Malware Analysis and Handling Playbook |
|
|---|---|
Cyber Deception Tactics and Strategy Playbook |
|
|---|---|
Intellectual Property Theft Prevention Playbook |
|
|---|---|
Secure Application Deployment Playbook |
|
|---|---|
Threat Intelligence Analysis Playbook |
|
|---|---|
Secure Network Architecture Design Playbook |
|
|---|---|
Critical Infrastructure Protection Scenarios Playbook |
|
|---|---|
Patch Management and Vulnerability Remediation Playbook |
|
|---|---|
Remote Access Trojans (RATs) Counteraction Playbook |
|
|---|---|
Cyber Espionage Simulation and Counter Playbook |
|
|---|---|
Dark Web Monitoring and Intelligence Playbook |
|
|---|---|
Intrusion Detection System Evasion Techniques Playbook |
|
|---|---|
Mobile Device Security Enforcement Playbook |
|
|---|---|
Quantum Computing Cryptography Challenges Playbook |
|
|---|---|
Third-Party Vendor Risk Assessment Playbook |
|
|---|---|
Security Operations Center (SOC) Efficiency Playbook |
|
|---|---|
Cyber Range Purple Team Exercises Playbook |
|
|---|---|
User Behavior Analytics for Insider Threats Playbook |
|
|---|---|
Advanced Network Traffic Analysis Playbook |
|
|---|---|
AI-Powered Threat Detection Scenario Playbook |
|
|---|---|
Data Loss Prevention (DLP) Tactics Playbook |
|
|---|---|
Secure Internet Gateway Configuration Playbook |
|
|---|---|
Advanced Application Layer Attack Playbook |
|
|---|---|
Remote Worker Security Challenges Playbook |
|
|---|---|
Brute Force Attack Defense and Mitigation Playbook |
|
|---|---|
Man-in-the-Middle (MITM) Attack Simulation Playbook |
|
|---|---|
Cyber Range Stress Testing and Load Balancing Playbook |
|
|---|---|
Secure API Development and Integration Playbook |
|
|---|---|
Lateral Movement Detection and Prevention Playbook |
|
|---|---|
Secure Data Storage and Retrieval Playbook |
|
|---|---|
Blockchain Security Implementation Challenges Playbook |
|
|---|---|
Secure Configuration Management Playbook |
|
|---|---|
DevSecOps for Serverless Architectures Playbook |
|
|---|---|
Securing Cloud Data with Encryption Best Practices Playbook |
|
|---|---|
Ransomware Attack Vector Isolation Playbook |
|
|---|---|