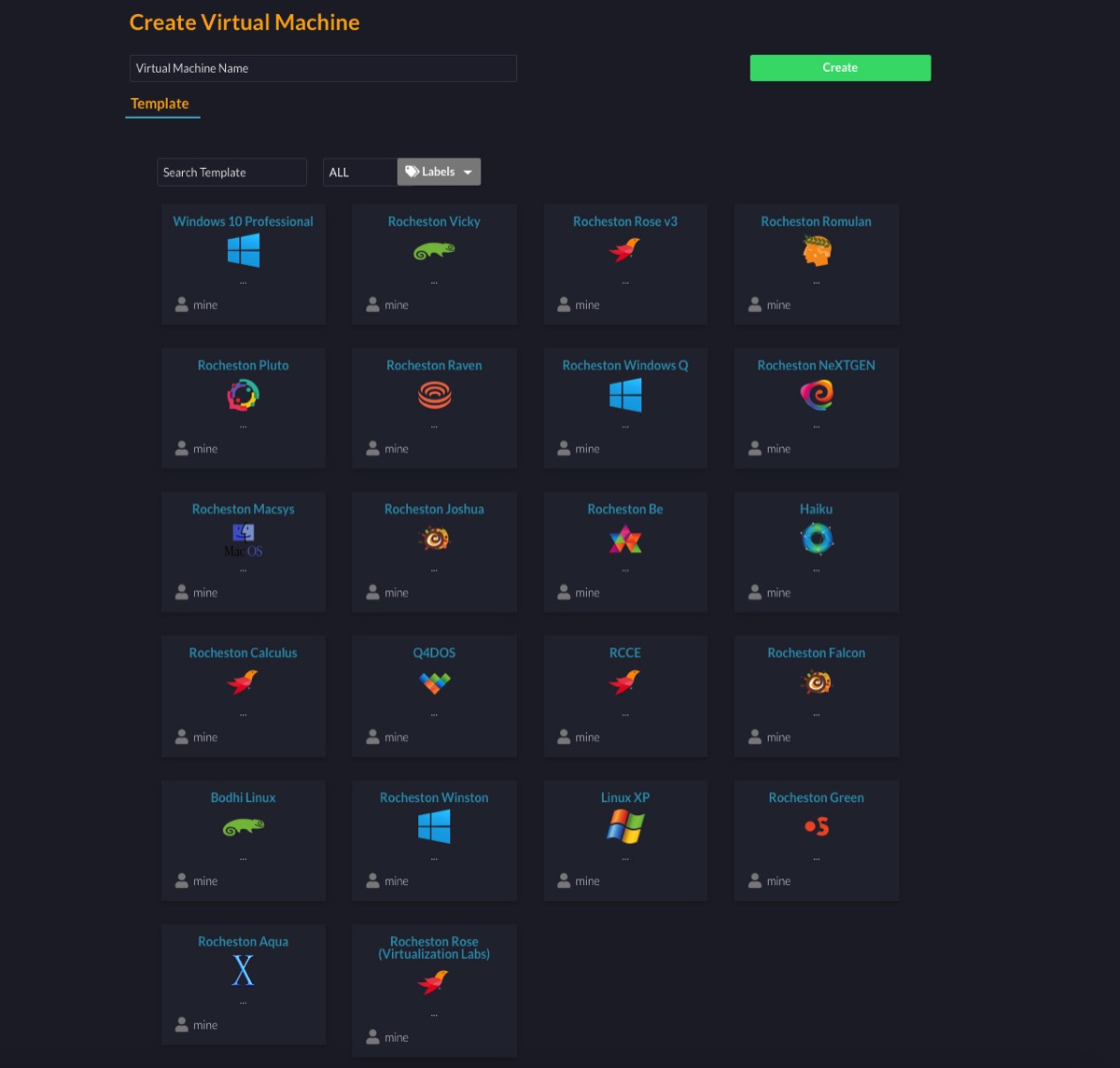
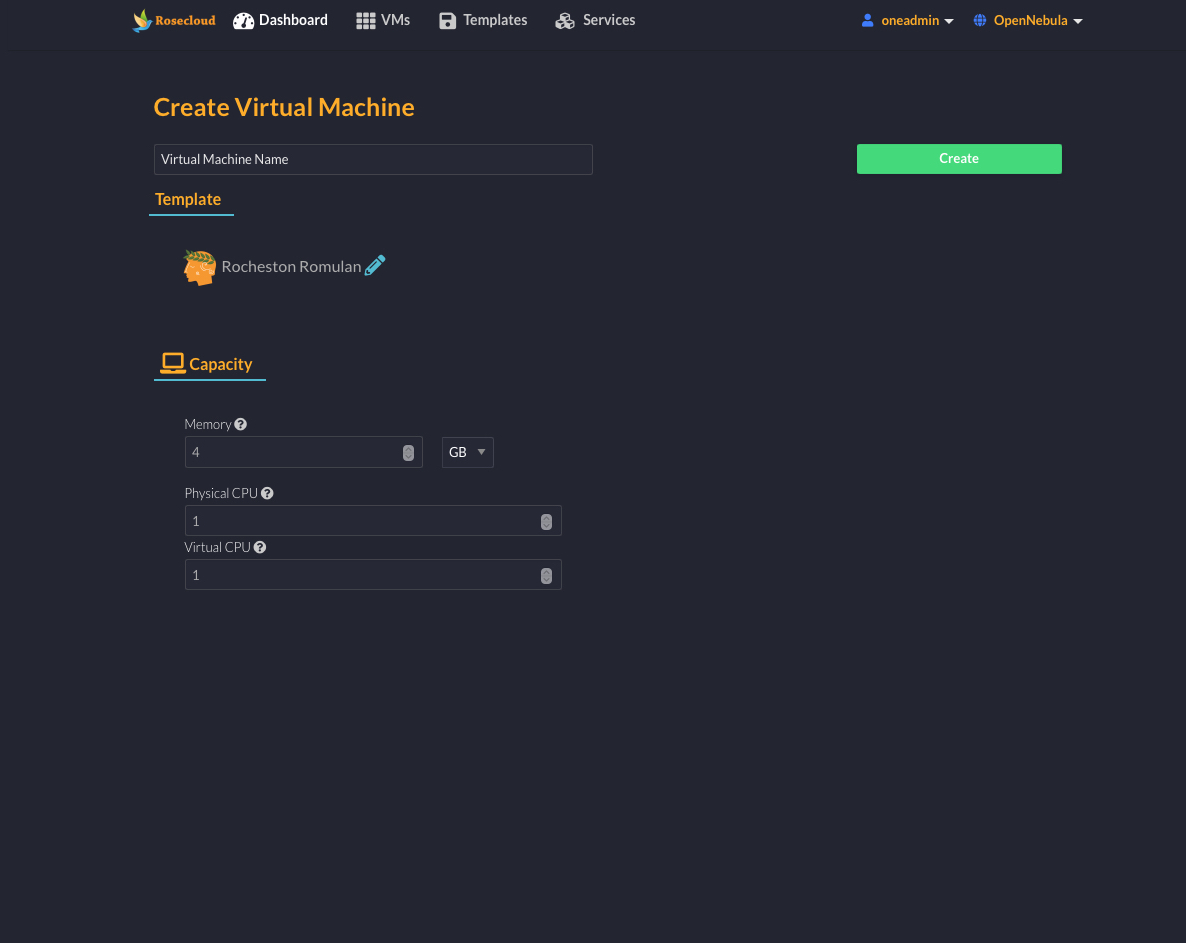
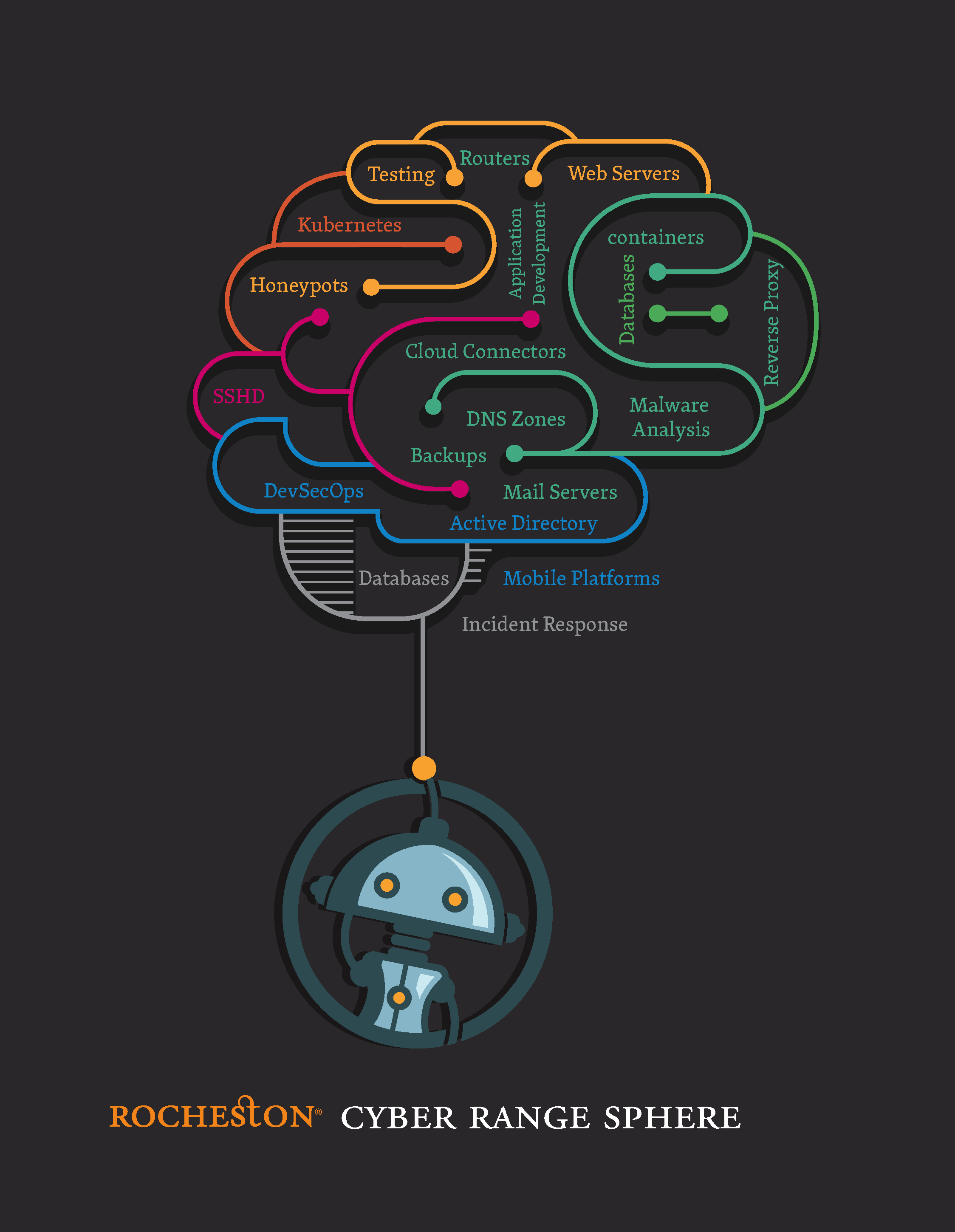
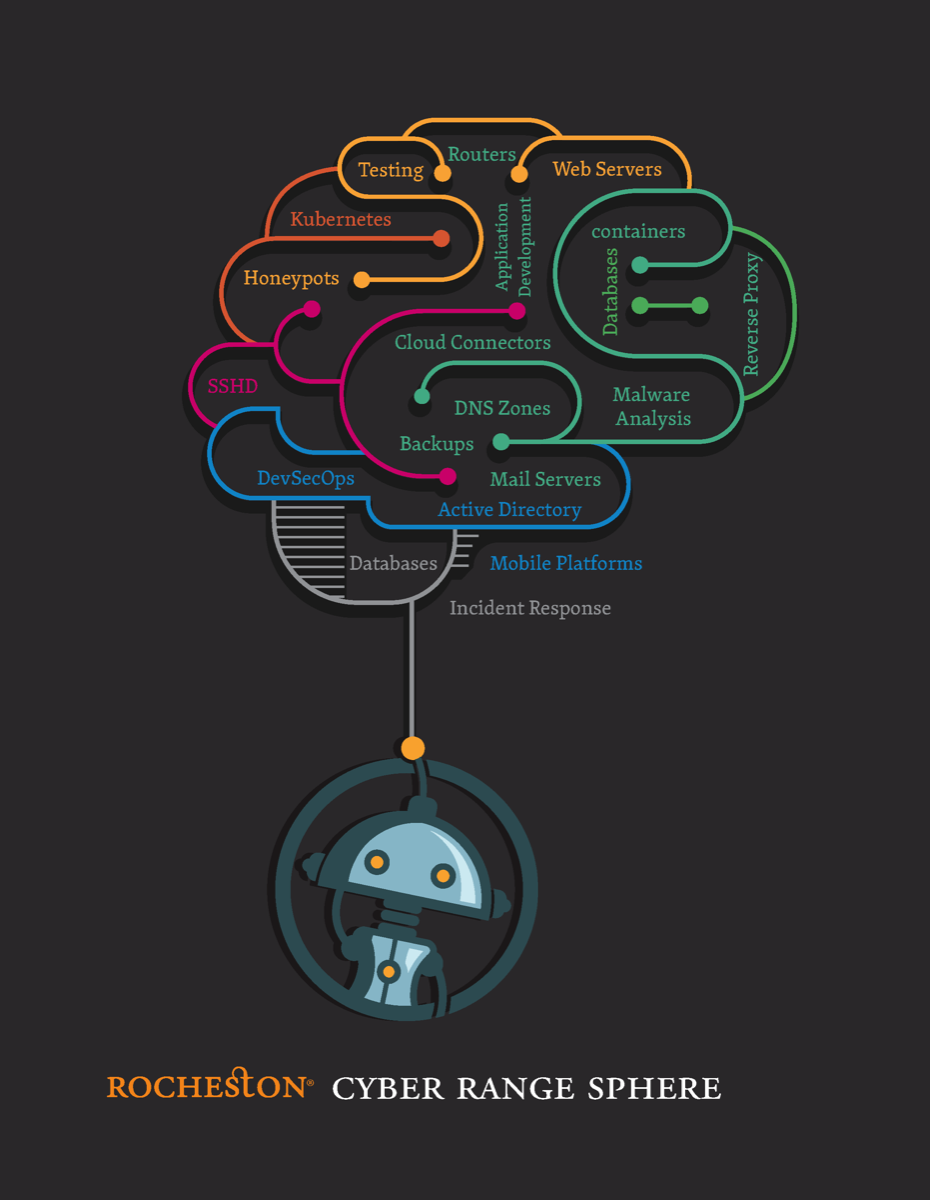
Rocheston Cyber Range Sphere
The Cyber Range Sphere is a simulation platform used in
RCCE® Level 2 training program. The Cyber Range Sphere helps in assessing incident response processes, and testing new technologies. A Cyber Range Sphere recreates the experience of responding to a cyberattack by replicating the organizational network infrastructure, and the attack itself. Cyber Range Sphere enables hands-on training in a controlled and secure environment.
Rocheston will offer the
most interactive cyber network training to equip your IT infrastructure, DevOps and SecOps teams to thwart the emerging cyber threats. By offering a cross-disciplinary training tool combined with an innovative and immersive team building experience, Cyber Range Sphere is an effective method to train all the front-line people for executing a comprehensive security strategy for the present and the future.
As a network becomes bigger, it is crucial to have a cutting-edge security insight and hand-on experience to protect it.
Cyber Range Sphere is an ideal way to:
- Build a unique Cyber Range Sphere with a select number of networks and security devices
- Research and thwart real-world threats in a controlled environment
- Identify and respond to live threats using the advanced Rocheston Rose platform with guidance from experienced instructors.
- Strengthen threat detection and response skills by exercising against other teams during cyberattack life-cycle scenarios.
- New cyberattack attack life-cycle scenarios and malware are added by Rocheston Cyberthreat Intelligence Center every week.
- Hands-on structured platform built in an orchestrated environment with a software-defined topology.